Difference between revisions of "Anonymising your traffic with linux"
From Gender and Tech Resources
m (Tag: VisualEditor) |
|||
| (96 intermediate revisions by one other user not shown) | |||
| Line 1: | Line 1: | ||
| − | + | Public networks like the internet are very vulnerable to traffic analysis. Packet headers identify the IP addresses of the recipient(s) and the packet routes can rather easily be tracked, see [[Networking concepts]]. | |
| − | + | Transmissions can be encrypted so that an attacker cannot learn the content of these transmissions, but this still reveals the fact that two parties are communicating. If for example a government official is sending encrypted data to a website of the opposition, and later that site publishes a document that was supposed to be secret, it is pretty clear what happened. | |
| − | + | To explain how enhanced communication anonymity can be reached on a linux platform, this page gives an overview of used approaches. The 3 major anonymity networks are Tor/Onionland, I2P/Garlicland and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three. Each anonymity network is designed for a different purpose. One network alone cannot do what the three can do together. Tor and I2P cannot persist information like Freenet can, Tor and Freenet can't offer the generic transports that I2P provides and Freenet doesn't handle data streaming as well as Tor and I2P. There is also no better proxy system than the Tor network. | |
| − | + | To get to the bones and see for yourself, check out the resulting traffic after making changes, for example with wireshark. And to not run into a wall during experimentation (aaaah, nothing works), punch the necessary holes in your firewall. If you adjusted your <code>/etc/sysctl.conf</code> you may want to learn how to use exception options (when available) for commands, or undo some of those changes. | |
== Plausible deniability == | == Plausible deniability == | ||
| − | Plausible deniability in networking is about relaying certain types of broadcasts automatically in such a way that the original transmitter of a file is indistinguishable from those who are merely relaying it allows for the person who first transmitted the file to claim that his computer had merely relayed it from elsewhere, and this claim cannot be disproven without a complete decrypted log of all network connections to and from that person's computer. | + | Plausible deniability in networking is about relaying certain types of broadcasts automatically in such a way that the original transmitter of a file is indistinguishable from those who are merely relaying it allows for the person who first transmitted the file to claim that his computer had merely relayed it from elsewhere, and this claim cannot be disproven without a complete decrypted log of all network connections to and from that person's computer, or ... |
| − | + | Plausible deniability has its limits. Recent cryptographic primitives and protocols offer a wide range of features besides confidentiality and integrity. There are many protocols that have more advanced properties such as forward secrecy, deniability or anonymity. In a phrack article a deeper look at deniability in communication (e.g. messaging) protocols appeared. One protocol that claims to offer deniability is OTR. The construction in the article can probably be extended in a quite general way. It shows the limits of deniability, especially in protocols that offer message integrity features (as OTR does). A protocol is constructed that enables each partner in a conversation to cooperate with an observing party, such that he can prove the authenticity of any message that was part of the conversation to the observing party <ref>Secure Function Evaluation vs. Deniability in OTR and similar protocols http://phrack.org/issues/68/14.html#article</ref>. | |
| − | == | + | == SSH tunneling == |
| − | == | + | === Tunneling with local port forwarding === |
| + | Imagine wikileaks being blocked using a proxy filter in a university somewhere. A SSH tunnel can be used to bypass this restriction. | ||
| − | + | Let’s name the machine at the university ''socially-correct'' and the home machine as ''home''. The ''home'' machine needs to have a public IP and be running a SSH server for this to work. You must have ssh user access on ''home'' and ''socially-incorrect'' must have access to <code>host:hostport</code> (is not blocked). | |
| − | === | + | $ ssh -L localport:host:hostport user@home -N |
| + | |||
| + | where: | ||
| + | * -L: port forwarding parameters | ||
| + | * localport: local port (choose a port that is not in use by other service) | ||
| + | * host: server that has the port (hostport) that you want to forward | ||
| + | * hostport: remote port | ||
| + | * -N: do not execute a remote command (you will not have the shell). | ||
| + | * user: user that has ssh access to the ssh server | ||
| + | * home: the machine/server running the ssh server that will be used for forwarding/tunneling | ||
| + | |||
| + | For example, to create the SSH tunnel execute following from the ''socially-correct'' machine: | ||
| + | |||
| + | $ ssh -L 9001:wikileaks.org:80 user@home | ||
| + | |||
| + | <pre> | ||
| + | +--------------+<-- port 22 -->+--------------+<-- port 80 -->+-----------+ | ||
| + | | SSH client |-----------------| SSH server |-----------------| host | | ||
| + | +--------------+ +--------------+ +-----------+ | ||
| + | localhost:9001 home wikileaks.org:80 | ||
| + | </pre> | ||
| + | Open a browser and go to http://localhost:9001 to see if the tunnel is working. | ||
| + | |||
| + | Now the SSH client at ''socially-correct'' will connect to the SSH server running at ''home'' (usually running at port 22) binding port 9001 of ''socially-correct'' to listen for local requests thus creating a SSH tunnel between ''home'' and ''socially-correct''. At the ''home'' end it will create a connection to ''wikileaks.org'' at port 80. So ''socially-correct'' doesn’t need to know how to connect to ''wikileaks.org''. Only ''home'' needs to worry about that. The channel between ''socially-correct'' and ''home'' will be encrypted while the connection between ''home'' and ''wikileaks.org'' will be unencrypted. | ||
| + | |||
| + | The ''home'' to ''wikileaks.org'' connection is only made when the browser makes the request, not at the tunnel setup time. | ||
| + | |||
| + | The SSH man pages say: | ||
| + | |||
| + | * <code>-L port:host:hostport</code> specifies that the given port on the local (client) host is to be forwarded to the given host and port on the remote side. This works by allocating a socket to listen to port on the local side, and whenever a connection is made to this port, the connection is forwarded over the secure channel, and a connection is made to host port hostport from the remote machine. Port forwardings can also be specified in the configuration file. Only root can forward privileged ports. IPv6 addresses can be specified with an alternative syntax: port/host/hostport | ||
| + | * <code>-N</code> Do not execute a remote command. This is useful for just forwarding ports (protocol version 2 only). | ||
| + | |||
| + | You can also use local port forwarding to set up a VNC session between ''socially-correct'' and your ''home'' server. From ''socially-correct'': | ||
| + | |||
| + | $ ssh -L 5900:localhost:5900 user@home | ||
| + | |||
| + | The <code>localhost</code> is relative to the gateway (''home'' in this case), not the machine from where the tunnel is initiated. So this will make a connection to port 5900 of the ''home'' computer where the VNC client would be listening in. | ||
| + | |||
| + | === Reverse tunneling with remote port forwarding === | ||
| + | |||
| + | What if we wish to connect to an internal university website from ''home''? The university firewall is blocking all incoming traffic. We can connect from ''home'' to the university internal network so that we can browse the internal site. We can initiate the tunnel from the ''socially-correct'' computer behind the firewall. This is possible since only incoming traffic is blocked and outgoing traffic is allowed. The client will now be at the ''home'' computer and instead of -L option we use -R which specifies a reverse tunnel is to be created. From ''socially-correct'': | ||
| + | |||
| + | $ ssh -R 9001:internalsite.org:80 user@home | ||
| + | |||
| + | The SSH client at ''socially-correct'' will connect to the SSH server running at ''home'' creating a SSH channel. The server will bind port 9001 on the ''home'' machine to listen for incoming requests that are then routed through the created SSH channel between ''home'' and ''socially-correct''. Now it’s possible to browse the internal site by visiting http://localhost:9001 in a web browser on the ''home'' machine. The ''socially-correct'' machine will then create a connection to internalsite.org and relay back the response to ''home'' via the created SSH channel. | ||
| + | |||
| + | === Dynamic port forwarding === | ||
| + | |||
| + | Dynamic port forwarding allows for configuring one local port for tunnelling data to all remote destinations. This requires the [[Networking_concepts#Socks_protocol|Socks protocol]]. At the client side of the tunnel a [[Networking_concepts#Socks_proxy|Socks proxy]] would be created and the application uses the Socks protocol to specify where the traffic should be sent when it leaves the other end of the ssh tunnel. From ''socially-correct'': | ||
| + | |||
| + | $ ssh -D 9001 user@home | ||
| + | |||
| + | SSH will create a Socks proxy listening in for connections at local port 9001 and when receiving a request routes the traffic via the SSH channel created between ''socially-correct'' and ''home''. Configure the browser to point to the Socks proxy at port 9001 at localhost. | ||
| + | |||
| + | == Virtual private networks == | ||
| + | |||
| + | === OpenVPN === | ||
| + | |||
| + | OpenVPN is free and open source software originally released in 2002. Since then it has become quite popular in the ease it can traverse wireless access points, firewalls, NAT-based routers, and HTTP proxy servers. By using OpenVPN it is possible to use different ports in order to bypass both firewalls and throttling. For more on OpenVPN and other options see [[Networking_concepts#Virtual_Private_Network_.28VPN.29|networking concepts: VPN]]. | ||
| + | |||
| + | Working with OpenVPN you will have the ability to work with OpenWRT or DD-WRT and run your local network on a single VPN account. In order to do this you will need to have an OpenVPN account, as well as a router that can be flashed, preferably OpenWRT. | ||
| + | |||
| + | ==== Routed vs bridged VPN ==== | ||
| + | |||
| + | Choose bridging only when: | ||
| + | * the VPN needs to be able to handle non-IP protocols such as IPX | ||
| + | * you are running applications over the VPN which rely on network broadcasts (such as LAN games) | ||
| + | * avoiding setting up a Samba or WINS server for m$ file sharing across the VPN. Better yet, just get rid of the m$ files and machines. | ||
| + | |||
| + | ==== Installing OpenVPN client ==== | ||
| + | |||
| + | If you are using a debian-based distro, you can use a package manager such as apt-get: | ||
| + | |||
| + | $ sudo apt-get install openvpn | ||
| + | |||
| + | It is also possible to install <code>openvpn</code> using the universal ./configure method. First expand the .tar.gz file: | ||
| + | |||
| + | $ tar xfz openvpn-[version].tar.gz | ||
| + | |||
| + | Then cd to the top-level directory, configure and install: | ||
| + | |||
| + | <pre>$ sudo ./configure | ||
| + | $ sudo make | ||
| + | $ make install</pre> | ||
| + | |||
| + | You can either use the VPN server you set up yourself, or an existing service. Several [[autonomous collectives]] offer services for activists. For bitmask see below. Set it up as described. | ||
| + | |||
| + | === Connection failures and DNS leaks === | ||
| + | |||
| + | [[File:Leaky-boat.jpg|480px|thumb|right]] | ||
| + | |||
| + | If you simply add a VPN using common instructions, it generally fails open. That means, if the VPN breaks down, because the connection is interrupted, traffic will be sent without the VPN. It's much safer when it fails closed, i.e. when the VPN connection breaks down, the whole internet connection must be down as long as the VPN connection isn't restored. | ||
| + | |||
| + | In addition to VPN connection failures, the other big threat to your anonymity when using a trusted VPN service is that of DNS leaks, which can result in your ISP being able to ‘see’ and monitor your online activity even though you think you are safely protected by an encrypted VPN tunnel. | ||
| + | |||
| + | ==== Using wireshark to check for leaks ==== | ||
| + | This is an example in a debian virtualbox VM, but is also valid in general for other setups. | ||
| + | |||
| + | Virtual machines receive their network address and configuration on the private network from a DHCP server integrated into VirtualBox. The IP address assigned to the virtual machine is on a completely different network than the host (but can be seen with [[Linux_security#wireshark|wireshark]] from the host). As more than one card of a virtual machine can be set up to use [[Networking_concepts#Network_address_translation_.28NAT.29|NAT]], the first card is connected to the private network 10.0.2.0, the second card to the network 10.0.3.0 and so on. | ||
| + | |||
| + | If you haven't installed wireshark yet, see [[Linux_security#wireshark|linux security: wireshark]] for installing and basic usage. | ||
| + | |||
| + | To check if you have DNS leaks, fire up wireshark: | ||
| + | * Start capturing on eth0 and connect to the VPN. | ||
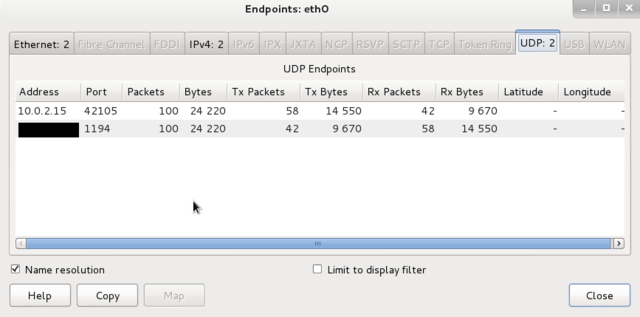
| + | * After capturing either a fixed number of packets, or an amount of data or for a specific time period, go to Statistics -> Endpoints | ||
| + | | ||
| + | [[File:Statistics-endpoints.png|348px|thumb|center]] | ||
| + | [[File:Statistics-endpoints2.png|640px|thumb|center]] | ||
| + | |||
| + | There should only be one public IP address, namely that of the VPN server that you’re connected to. | ||
| + | |||
| + | ==== Setting DNS nameservers in debian ==== | ||
| + | |||
| + | Resolver libraries look to <code>/etc/resolv.conf</code> for a list of nameservers. In the simplest case, that is the file to edit to set the list of name servers. And various other programs for dynamic configuration will be happy to overwrite your settings: | ||
| + | |||
| + | * The resolvconf program | ||
| + | * The network-manager daemon | ||
| + | * DHCP clients | ||
| + | |||
| + | In most situations, the file to edit is the configuration file for such a program. | ||
| + | |||
| + | Fail: | ||
| + | |||
| + | <pre># Dynamic resolv.conf(5) file for glibc resolver(3) generated by resolvconf(8) | ||
| + | # DO NOT EDIT THIS FILE BY HAND -- YOUR CHANGES WILL BE OVERWRITTEN</pre> | ||
| + | |||
| + | In case the network you hook into uses DHCP and you set your DNS nameservers (in debian) manually in <code>/etc/resolv.conf</code>, any change will be lost as it gets overwritten next time something triggers resolvconf. And adding nameservers after a loopback in interfaces doesn’t work either. | ||
| + | |||
| + | <code>resolvconf</code> is a set of script and hooks managing DNS resolution using DHCP client hooks, a network manager plugin and <code>/etc/network/interfaces</code> to generate a list of nameservers and domain to put in <code>/etc/resolv.conf</code> | ||
| + | |||
| + | The <code>/etc/resolvconf/resolv.conf.d</code> directory (probably) contains base, head, original and tail files in resolv.conf format: | ||
| + | |||
| + | * base: used when no other data can be found | ||
| + | * head: for the header of resolv.conf, can be used to ensure a DNS server is always the first one in the list | ||
| + | * original: backup of your resolv.conf at the time of resolvconf installation | ||
| + | * tail: appended at the end of the resulting resolv.conf | ||
| + | |||
| + | Open the head file with your favorite editor for it (geany, vi, vim, nano) as root (sudo, su or root terminal). The head file contains the same warning as above … but in this case it is there so that when the resolv files are constructed, the warning will ultimately work its way into the resulting <code>resolv.conf file</code>. | ||
| + | |||
| + | Add (or replace) the nameservers you picked from for example, the opennic project or the wikileaks alternative DNS list: | ||
| + | |||
| + | <pre>nameserver nnn.nnn.nnn.nnn | ||
| + | nameserver nnn.nnn.nnn.nnn</pre> | ||
| + | |||
| + | Then update: | ||
| + | $ sudo resolvconf -u | ||
| + | |||
| + | And test by viewing the results in <code>/etc/resolv.conf</code>. You can also create <code>/etc/resolv.conf.tail</code>, but do check because only the first two are used. | ||
| + | |||
| + | ==== Punching holes in ufw for a VPN ==== | ||
| + | |||
| + | To forcibly prevent DNS leaks use a firewall. <code>ufw</code> can be set up as a fail safe mechanism (aka kill switch). | ||
| + | |||
| + | [[Linux_security#ufw_and_gufw|Install ufw]] if not already installed. | ||
| + | |||
| + | Set all traffic to deny: | ||
| + | |||
| + | <pre>$ sudo ufw default deny outgoing | ||
| + | $ sudo ufw default deny incoming</pre> | ||
| + | |||
| + | Permit OpenVPN traffic (if using OpenVPN adapter is probably <code>tun0</code> but [[Kinky_linux_command-line#Network_connections|check]]) | ||
| + | |||
| + | $ sudo ufw allow out on tun0 from any to any | ||
| + | |||
| + | For added security you may want to keep incoming traffic disabled but if desired or required then allow it: | ||
| + | |||
| + | $ sudo ufw allow in on tun0 from any to any | ||
| + | |||
| + | With this rule all non VPN traffic (and subsequently DNS requests not routed though VPN) will be blocked. | ||
| + | |||
| + | But, this set up requires that you disable the firewall to connect to the VPN and then enable it once connection is made. To allow establishment of a connection to the VPN server even when the firewall is enabled: | ||
| + | |||
| + | $ sudo ufw allow out from any to [VPN server IP address] | ||
| + | |||
| + | Add multiple rules for all VPN servers you will be using. If you want more strict rules and better security then only allow desired ports on <code>tun0</code>. | ||
| + | |||
| + | ==== Using the VPNfirewall script ==== | ||
| + | |||
| + | The VPNfirewall script by Adrelanos: | ||
| + | |||
| + | * Forbids outgoing traffic after the VPN software broke down for some reason. | ||
| + | * Has tight firewall rules, using iptables policy drop. | ||
| + | * Only tested with OpenVPN. Should work with other VPN clients such as PPTP in theory, you should test if it does what it claims anyway. | ||
| + | * Only tested on Debian Wheezy and Whonix. Should work on any other Linux distribution in theory, you should test if it does what it claims. | ||
| + | * Open Source / Free Software | ||
| + | |||
| + | More here, including how to install it: https://github.com/adrelanos/VPN-Firewall | ||
| + | |||
| + | === Bitmask === | ||
| + | |||
| + | Bitmask is an open source application to provide easy and secure encrypted communication. You can choose among several different service providers or start your own. Currently, Bitmask supports encrypted internet (VPN) with encrypted email coming soon. https://bitmask.net/ | ||
| + | |||
| + | == Publishing with freenet == | ||
| + | |||
| + | Freenet uses UDP and is the "oldest" of the 3 networks. Freenet is an anonymous data publishing network and very different from Tor and I2P. Freenet is much higher latency and focuses more on friend to friend interactions with often military grade security. It is slow and very resource intensive. | ||
| + | |||
| + | Freenet is a tool for bypassing totalitarian censorship where people would be killed for publishing certain content. It is not for casual browsing. https://freenetproject.org/ | ||
| + | |||
| + | == Proxying with tor == | ||
| + | |||
| + | Tor is an anonymous internet proxy using [[Networking_concepts#Onion_routing|onion routing]]. In an onion network, messages are encapsulated in layers of [[Encrypting_everything#Diffie-Hellman_key_agreement|encryption]], analogous to layers of the vegetable onion. The encrypted data is transmitted through a series of network nodes called onion routers, each of which "peels" away a single layer, uncovering the data's next destination. When the final layer is decrypted, the message arrives at its destination. The sender is thought to remain anonymous because each intermediary knows only the location of the immediately preceding and following nodes. Connections with Tor aren't dynamic like I2P tunnels are, Tor circuits persist until closed. This can reduce anonymity. There is no support for UDP. | ||
| + | |||
| + | The best use for Tor is anonymous proxying to the regular internet. It is the most sophisticated and robust system for proxying currently devised. And despite Tor being a powerful tool, [[Networking_concepts#Vulnerabilities_3|it is possible to distinguish Tor traffic from normal traffic, and it is possible to perform correlation-based attacks to de-anonymise our use of it]]. | ||
| + | |||
| + | === Browser bundle === | ||
| + | |||
| + | The Firefox-based Tor Browser Bundle integrates the Tor network's enhanced privacy and security. It includes the Vidalia network connection utility. It's installation is easy and it works out of the box. https://www.torproject.org/projects/torbrowser.html.en | ||
=== Liberté linux, tails, whonix, freepto === | === Liberté linux, tails, whonix, freepto === | ||
| − | + | There are also a few distro's and live CD/DVD's focused on anonymity that are based on use of tor. | |
| − | + | Really, comparisons are useless, except for making it easier to choose which one suits a specific purpose and environment best. | |
| − | + | ||
| − | + | ''These tables are a year old, and need revisiting, checking and updating. Also, Freepto will need to be tried out further and added.'' | |
| − | ==== | + | ==== General ==== |
| + | {| class="wikitable" | ||
| + | |- | ||
| + | ! Liberté linux !! Tails !! Whonix !! Freepto | ||
| + | |- | ||
| + | | Liberté Linux<ref>Liberté Linux http://dee.su/liberte</ref> is a secure<ref>Liberté security http://dee.su/liberte-security</ref>, reliable, lightweight and easy to use <ref>Liberté Linux Documentation http://dee.su/liberte-documentation</ref> Gentoo-based LiveUSB/SD/CD Linux distribution with the primary purpose of enabling anyone to communicate safely and covertly in hostile environments <ref>Liberté Linux motivation http://dee.su/liberte-motivation</ref>. Whether you are a privacy advocate, a dissident, or a sleeper agent, you are equally likely to find Liberté Linux useful as a mission-critical communication aid. || Tails <ref>Tails https://tails.boum.org</ref> is a live operating system <ref>Wikipedia LiveUSB https://en.wikipedia.org/wiki/Live%5FUSB</ref>, that you can start on almost any computer from a DVD, USB stick, or SD card. It aims at preserving your privacy and anonymity, and helps you to use the Internet anonymously and circumvent censorship; leave no trace on the computer you are using unless you ask it explicitly and use state-of-the-art cryptographic tools to encrypt your files, emails and instant messaging. || Whonix <ref>Whonix https://www.whonix.org/wiki/Main_Page</ref> is an Anonymous Operating System. It hides your IP/location and uses Tor to anonymize your data traffic. This means that neither the contacted server, nor any eavesdropper on your connections, nor the operators of the Tor network themselves can realize which webservice you use. || Freepto <ref>Freepto http://avana.forteprenestino.net/freepto/</ref> is a live operating system aiming to be a powerful tool for activists, journalists, whistleblowers, and people that want to protect their privacy. Runs entirely on a USB key. Uses the Metadata Anonymisation Toolkit <ref>Metadata Anonymisation Toolkit https://mat.boum.org</ref>. | ||
| + | |- | ||
| + | | Hardened Gentoo kernel <ref>Hardened Gentoo kernel http://www.gentoo.org/proj/en/hardened/</ref>, which includes all grsecurity/PaX security enhancements <ref>grsecurity/PaX http://grsecurity.net/</ref>. || Debian based <ref>Debian http://www.debian.org/</ref> || Debian based || Debian based | ||
| + | |- | ||
| + | | HDD, bootable media, virtualized environments (but was developed for USB) || Bootable media, virtualized environments (but was developed for LiveCD) || HDD (but such an install misses the point of isolation via VirtualBox), virtualized environments || Bootable media | ||
| + | |- | ||
| + | | Relatively young || Well tested and peer reviewed || Relatively young || Young | ||
| + | |- | ||
| + | | Lightweight but do not be put off by its small image size — Liberté Linux is a fully capable distribution with HTML5 video support in the browser, file managers and chat plugins, audio players, a multitude of multilingual fonts, full application interface and keyboard localization, and much more. || Balance between functionality and available space and security || An anonymous general purpose operating system || An anonymous general purpose operating system | ||
| + | |- | ||
| + | | Pseudonymous dev || Non-anonymous dev team || Non-anonymous dev || Under development by ''AvANa''<ref>AvANa http://avana.forteprenestino.net/</ref>, the resident hacktivist collective of Forte Prenestino<ref>Forte Prenestino http://www.forteprenestino.net/</ref>, one of the oldest and most famous social centrer (squat) in Italy. | ||
| + | |} | ||
| − | ==== Freepto ==== | + | ==== Memory matters ==== |
| + | |||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | ! Liberté Linux !! Tails !! Whonix !! Freepto | ||
| + | |- | ||
| + | | Download size is 200+ MB || Download size is 800+ MB || You need to download VirtualBox and both Gateway and Workstation virtual machine images. Both VMs together are currently almost 2 GB || Download size is ~ 1.0 GB | ||
| + | |- | ||
| + | | Installed 220+ MB || Installed 1500+ MB || VirtualBox will need about 30 MB of hard disk space, the VM’s 2GB, plus the virtual disk sizes set in the VM’s || | ||
| + | |- | ||
| + | | Can run from USB stick with other files. Remaining space can be used even in windows. || Uses all space on the usb stick. Remaining space is wasted or made persistent. || Virtual disks on hosts || | ||
| + | |- | ||
| + | | persistent is an encrypted file on USB. It can be viewed in Windows with FreeOTFE. You can create your own encrypted containers from command line with <code>otfe</code> || persistent is a partition on USB space. Cannot be viewed in Windows, meaning, we don’t know how to view it. Yet. || Full persistence. You can add full disk encryption to host, and use file encryption in guest to your liking. || | ||
| + | |- | ||
| + | | Runs with 192 MB RAM || Needs a lot of RAM || Setting the Virtual Machine RAM to use less than 512MB will boot the workstation into console mode || | ||
| + | |} | ||
| + | |||
| + | ==== User friendliness ==== | ||
| + | |||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | ! Liberté Linux !! Tails !! Whonix !! Freepto | ||
| + | |- | ||
| + | | Runs on older PCs. || Is a headache on older PCs or on PCs with small memory. And with every new version shipped older and newer PCs become too old. || Whonix has higher hardware requirements, and therefore more space to implement features. || | ||
| + | |- | ||
| + | | Upgrading by overwriting files (even from windows). Installing software on Liberte is not for newbies: there is no way to install software into its root tree — both due to lack of toolchain and portage, and due to read-only mode of most of the filesystem. The only way of adding software is building a custom image, or using portable binaries (provided that their required libraries are available). See [[Making_our_own_linux_images|making our own LiveCD/DVD images]]. | ||
| + | || Upgrading and installing additional software can be done from bootable medium. || Upgrading and installing additional software can be done from guest using Apper or Synaptic package. || | ||
| + | |} | ||
| + | |||
| + | ==== Applications ==== | ||
| + | |||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | ! Liberté Linux !! Tails !! Whonix !! Freepto | ||
| + | |- | ||
| + | | Browser: Epiphany plus patches. Opens a menu page. || Browser: Iceweasel. Default opening page is set to “check.torproject.org” || Browser: Tor Browser with extensions || | ||
| + | |- | ||
| + | | Password Management: Figaro’s Password Manager || Password Management: KeePassX || Choice || | ||
| + | |- | ||
| + | | Pidgin (with OTR) is “empty” by default || Pidgin client comes pre-configured with an OFTC account over SSL and a nickserv || Choice of chat clients || | ||
| + | |- | ||
| + | | Claws is pre-configured with a “cables” account (on pendrive only). Cables is a p2p message system on a Claws email GUI. Both sender and receiver need to “see” each other to exchange “emails”. Can cost up to half an hour before your Cables node is discoverable by the other party || Claws installs “empty” || Mozilla Thunderbird with TorBirdy || | ||
| + | |- | ||
| + | | XChat (with SASL) || XChat || XChat in Whonix has been hardened according to TorifyHOWTO/XChat <ref>TorifyHOWTO/XChat https://trac.torproject.org/projects/tor/wiki/doc/TorifyHOWTO/XChat</ref> || | ||
| + | |} | ||
| + | |||
| + | ==== Security ==== | ||
| + | |||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | ! Liberté Linux !! Tails !! Whonix !! Freepto | ||
| + | |- | ||
| + | | || When using mobile phone connectivity, such as 3G or GSM, the identifier of your SIM card (IMSI) and the serial number of your phone (IMEI) are always revealed to the mobile phone operator. <ref>Are hardware serial numbers hidden in TAILS? https://tails.boum.org/doc/first_steps/startup_options/mac_spoofing/index.en.html</ref> || Most dangerous leaks are protected and many default applications are already configured, not to leak<ref>Protocol-Leak-Protection and Fingerprinting-Protection https://www.whonix.org/wiki/Protocol-Leak-Protection_and_Fingerprinting-Protection</ref>|| | ||
| + | |- | ||
| + | | Mac Changer: tries to perform a mac address change at startup. || The uniqueness of MAC addresses introduce two types of potential issues for Tails users, in particular if the MAC address can be linked to the user's identity. Spoofing the MAC address is the natural solution. Unfortunately, in some cases MAC spoofing may cause network connection issues or even raise alarms; care should be taken to prevent MAC spoofing in such situations. <ref>Mac Changer: MAC address anonymization is under development https://tails.boum.org/contribute/design/MAC_address/</ref> || There is no support for MAC address use in this domain. This is still an open research problem. <ref>Mac Address https://www.whonix.org/wiki/Pre_Install_Advice#MAC_Address</ref> || | ||
| + | |- | ||
| + | | Amnesic || Amnesic || Not amnesic || | ||
| + | |- | ||
| + | | The only way to become root is by logging out during first 2 minutes after boot, then press Alt-F2, then run passwd. 😀 || In case Tails gets rooted, the adversary can bypass the firewall and get the user’s real IP. || The Workstation is the place where the browser, IRC client and so on is running. The Gateway is the place where Tor and the firewall is running. The Whonix-Workstation is unaware of its external IP. || | ||
| + | |- | ||
| + | | || The Tails developers have plans to implement persistent entry guards <ref>Persistence preset: Tor state https://labs.riseup.net/code/issues/5462</ref>. That ticket also contains additional extra information, such as a link to a discussion about a missing feature: Location-aware persistent guards <ref>[tor-talk] Location-aware persistent guards https://lists.torproject.org/pipermail/tor-talk/2012-October/025975.html</ref>. In an ideal world, users could enter a pin/token/password to choose various sets of entry guards <ref>Support more stable guards for live CDs https://trac.torproject.org/projects/tor/ticket/2653</ref> || You could consider to always use non-persistent entry guards. In most cases, this is something to avoid because persistent entry guards is a security feature as explained in the introduction. A more secure, but more time expensive approach would be Alternating Bridges. <ref>Non-Persistent Entry Guards https://www.whonix.org/wiki/Tor#Non-Persistent_Entry_Guards</ref> || | ||
| + | |- | ||
| + | | NTP is the only application that potentially must communicate in the clear — to a known server pool. NTP is not necessary for correct operation of Liberté, and it is currently turned off to prevent timestamp-based fingerprinting and MIM DoS attacks. Torified HTP adjusts the time very reliably — albeit with less precision. In general, Tor requires a correct computer clock to start up, but in Liberté this problem is circumvented using a consensus-based time estimate. || Uses consensus (waits up to 150 seconds twice, restarting Tor in between), checks authority certificate, sets the system time to the valid-after of the unverified consensus Tor fetched, which will guarantee that the certificate and consensus are all valid. Then restarts Tor (since it behaves badly with time jumps during the early bootstrap stages) and waits until it accepts the consensus and finishes the bootstrap. HTP is then through Tor to get a more correct system time. <ref>Tails Design: Time syncing https://tails.boum.org/contribute/design/Time_syncing/</ref> || Whonix leaves the host's system clock or time synchronization mechanism untouched. | ||
| + | Whonix-Gateway and Whonix-Workstation are based on VirtualBox and therefore have their own virtual hardware system clocks. Most VirtualBox time synchronization features get disabled by Whonix. <ref>Whonix Design: TimeSync https://www.whonix.org/wiki/Dev/TimeSync</ref> || | ||
| + | |- | ||
| + | | || Until an audit of the bundled network applications is done, information leakages at the protocol level should be considered as − at the very least − possible <ref>Applications audit https://labs.riseup.net/code/issues/5769</ref> || Whonix security in real world <ref>Whonix security in real world https://www.whonix.org/wiki/Security_in_Real_World</ref> || | ||
| + | |- | ||
| + | | || We want to enable IsolateDestAddr and IsolateDestPort for the SocksPort used by most applications, unless we tell them otherwise.<ref>Tails separate Tor streams https://labs.riseup.net/code/issues/5334</ref> || Whonix implements protection against identity correlation through circuit sharing, however, for better privacy, you are still advised to understand a bit of the technical background. <ref>Stream Isolation https://www.whonix.org/wiki/Stream_Isolation</ref> || | ||
| + | |- | ||
| + | | || To make it difficult to distinguish Tails users, Tor Browser in Tails tries to provide the same information as Tor Browser on other operating systems in order to have similar fingerprints. <ref>Tails Fingerprint Page https://tails.boum.org/doc/about/fingerprint/index.en.html</ref> || To make it difficult to distinguish Whonix users from Browser bundle users, Whonix includes the Browser bundle and therefore should provide the same information as the Browser bundle in order to have similar fingerprints. <ref>Whonix Fingerprint Page https://www.whonix.org/wiki/Fingerprint</ref> || | ||
| + | |- | ||
| + | | All volatile memory is thoroughly erased upon shutdown in order to prevent cold boot attacks — whether an orderly shutdown, or an immediate one due to abrupt removal of the boot media. || To prevent cold boot attacks, the data in RAM is overwritten by random data when shutting down Tails. This erases all traces from your session on that computer. <ref>Protection against cold boot attacks https://tails.boum.org/doc/advanced_topics/cold_boot_attacks/index.en.html</ref>|| No protection from cold boot attacks || | ||
| + | |} | ||
| + | |||
| + | === Tor on host === | ||
| + | |||
| + | If you also wish to use other applications than browsing and/or you wish to chain, install tor on your box. | ||
| + | |||
| + | ==== Installing tor and privoxy ==== | ||
| + | |||
| + | For installing tor follow the instructions give by the tor project https://www.torproject.org/docs/debian.html.en#ubuntu | ||
| + | |||
| + | For installing privoxy http://www.privoxy.org/user-manual/installation.html | ||
| + | |||
| + | ==== Configuring privoxy ==== | ||
| + | |||
| + | When using socks5 on port %d, your application is giving Tor only an IP address. Applications that do DNS resolves themselves may leak information. So using Socks4A instead is a good idea. More on that here https://www.torproject.org/docs/faq#WarningsAboutSOCKSandDNSInformationLeaks. | ||
| + | |||
| + | Open <code>/etc/privoxy/config</code>, check that the listen address is <code>127.0.0.1:8118</code>, and set forward in privoxy to tor with <code>forward-socks4a / 127.0.0.1:9050 .</code> (Do NOT forget that point at the end). Save. | ||
| + | |||
| + | [[File:Listen-address.png|640px|thumb|center]] | ||
| + | |||
| + | [[File:Forward-socks4a.png|640px|thumb|center]] | ||
| + | |||
| + | Temporarily set your system wide network settings or the network settings in your browser to Manual Proxy configuration with Host or IP Adress 127.0.0.1 and port 9050. Check with http://check.torproject.org that it works. If it doesn’t work, maybe this faq helps https://www.torproject.org/docs/faq#DoesntWork | ||
| + | |||
| + | Undo the network settings: Set both, system wide and browser network settings to automatic, configure clients with IP address 127.0.0.1 and chosen port(s), and set up multiple circuits for separating streams. Whonix https://www.whonix.org/ and Tails are great to learn from. | ||
| + | |||
| + | ==== Transparently routing traffic through tor ==== | ||
| + | |||
| + | Requires [[Linux_security#iptables_and_netfilter|iptables]]: | ||
| + | |||
| + | * https://trac.torproject.org/projects/tor/wiki/doc/TransparentProxy | ||
| + | * https://help.ubuntu.com/community/TorDedicatedUser | ||
| + | |||
| + | ==== Configuring browser ==== | ||
| + | With IE, Opera and Safari there are too many ways that our privacy can be breached, and because of their closed design it is really hard to do anything about such privacy problems, hence the focus on Firefox and Konquerer. | ||
| + | |||
| + | In Firefox go to Edit —> Preferences —> Advanced tab —> Connection (Click Settings … button). | ||
| + | |||
| + | For an example of setting proxies (and switching between proxies) see [[Anonymising_your_traffic_with_linux#I2p_and_tor_in_iceweasel_using_foxyproxy_patterns|foxyproxy]]. | ||
| + | |||
| + | ==== Configuring xchat ==== | ||
| + | |||
| + | ==== Torbirdy for icedove ==== | ||
| + | |||
| + | ==== Configuring console-based applications with proxychains ==== | ||
| + | |||
| + | For using Tor with console based “clients”, applications that do not have any settings for adding proxy addresses, add the command “proxychains” in front of your commands. We can also add elinks, Elinks, a ‘text-browser’ that makes it possible to browse the internet without displaying images (Images and other media like pdf’s can optionally be displayed). | ||
| + | |||
| + | Install proxychains and elinks: | ||
| + | |||
| + | $ apt-get install proxychains elinks | ||
| + | |||
| + | Open <code>/etc/proxychains.conf</code> and check the following line exists (if not, add it): <code>socks4 127.0.0.1 9050</code> | ||
| + | [[File:Proxychains.png|724px|thumb|center]] | ||
| + | |||
| + | Check that it works by running the following commands and comparing results: | ||
| + | |||
| + | $ proxychains elinks cmyip.com | ||
| + | |||
| + | and | ||
| + | |||
| + | $ elinks cmyip.com | ||
| + | |||
| + | If wurks, you can for example anonymously run <code>nmap</code> anysite.com: | ||
| + | |||
| + | $ proxychains nmap [anysite.com] | ||
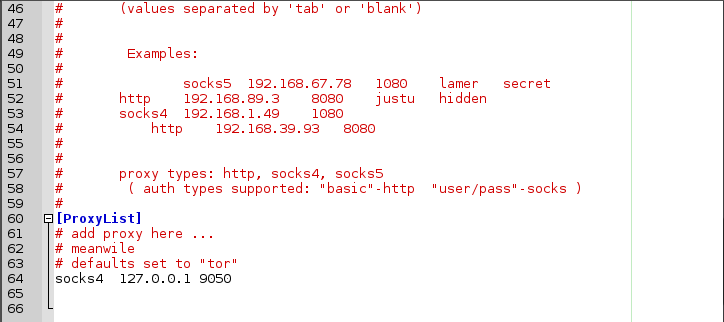
== Chaining == | == Chaining == | ||
| Line 38: | Line 397: | ||
== Going underground with i2p == | == Going underground with i2p == | ||
| + | |||
| + | I2P is a Distributed Peer to Peer Anonymous Network Layer that is strictly message-based (like IP), but there is a library available to allow reliable streaming communication on top of it (similar to TCP, although from version 0.6 there is a new UDP-based SSU transport). It allows you to send data between computers running I2P anonymously with multilayer end to end encryption. The name I2P derived from Invisible IRC Project (IIP) which was one of FreeNet's sister projects. I2P focuses on exclusively internal communication and not proxying to the regular internet. I2P uses [[Networking_concepts#Garlic_routing|garlic routing]] which involves clumping packets together into bigger packets. The combination of garlic routing, multilayer encryption -even the end points ("destinations") are cryptographic identifiers- and random padding on packets makes analysis of the content and detection of the origin of I2P traffic by third-party observers highly impractical if not nearly impossible. | ||
| + | |||
| + | The best use for I2P is for peer to peer file sharing and a replacement for the regular internet in the event that it gets bad enough to warrant such action. | ||
| + | |||
| + | === Installing === | ||
| + | |||
| + | Install according to the guides on this page: https://geti2p.net/en/download/debian | ||
| + | |||
| + | === Starting up automagically === | ||
| + | |||
| + | Add <code>i2prouter start</code> to your start up applications, and reboot. You can also set up i2p to boot before you even login: | ||
| + | |||
| + | $ sudo dpkg-reconfigure i2p | ||
| + | |||
| + | In which case you may have to do some port forwarding. | ||
| + | |||
| + | Set browser to always use Private Browsing. You can still use bookmarks to remember your most used pages. | ||
| + | Reboot and wait for the i2p router console to come up. | ||
| + | |||
| + | === ufw rules === | ||
| + | |||
| + | == I2p and tor in iceweasel using foxyproxy patterns == | ||
| + | |||
| + | === Prelims === | ||
| + | * Install tor and i2p | ||
| + | * Add FoxyProxy plugin/extension to Iceweasel/Firefox http://getfoxyproxy.org/ | ||
| + | |||
| + | === Patterns === | ||
| + | |||
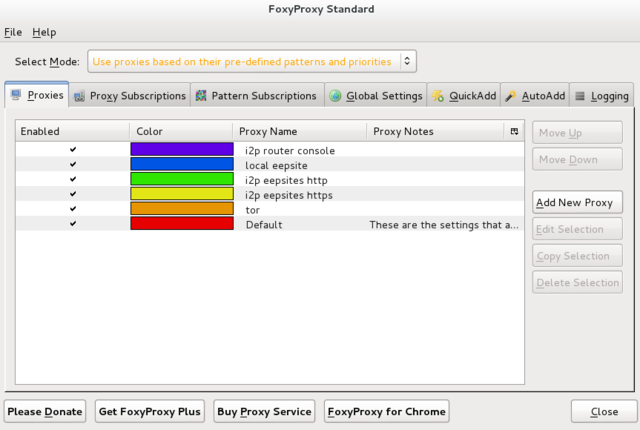
| + | I made use of a rainbow of colors that tell me what I am using while I browse, ending in red (default proxy), warning me I am naked. Note that order matters. For more on regular expressions see [[Kinky_linux_command-line#Regular_expressions|Kinky linux command-line: Regular expressions]]. | ||
| + | |||
| + | [[File:Rainbow.png|640px|thumb|center]] | ||
| + | |||
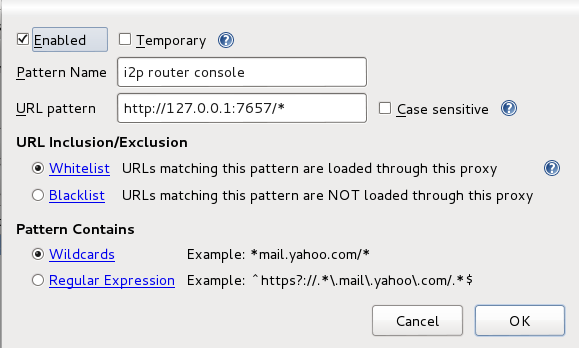
| + | ==== i2p router console ==== | ||
| + | |||
| + | General: Set name and color and check boxes Enabled, Animate, Include this proxy | ||
| + | |||
| + | Proxy Details: Direct internet connection (no proxy) | ||
| + | |||
| + | Pattern: Wildcard: <code>http://127.0.0.1:7657/*</code> | ||
| + | [[File:I2prouterconsole.png|579px|thumb|center]] | ||
| + | ==== local eepsite ==== | ||
| + | |||
| + | General: Set name and color and check boxes Enabled, Animate, Include this proxy | ||
| + | |||
| + | Proxy Details: Direct internet connection (no proxy) | ||
| + | |||
| + | Pattern: Wildcard: <code>http://127.0.0.1:7658/*</code> | ||
| + | |||
| + | ==== i2p eepsites http ==== | ||
| + | |||
| + | General: Set name and color and check boxes Enabled, Animate, Include this proxy | ||
| + | |||
| + | Proxy Details: Manual Proxy Configuration: Host or IP Address: 127.0.0.1 Port 4444 | ||
| + | |||
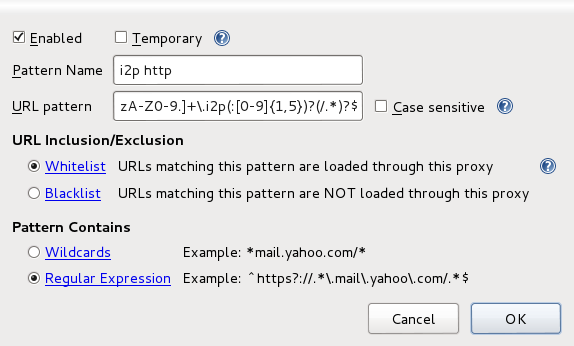
| + | Pattern: Regular Expression: <code>^http://[-a-zA-Z0-9.]+\.i2p(:[0-9]{1,5})?(/.*)?$</code> | ||
| + | |||
| + | [[File:I2phttp.png|574px|thumb|center]] | ||
| + | |||
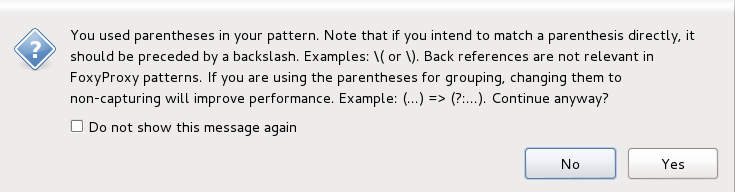
| + | You will get this message. Just click Yes. | ||
| + | |||
| + | [[File:Warning.png|735px|thumb|center]] | ||
| + | ==== i2p eepsites https ==== | ||
| + | |||
| + | General: Set name and color and check boxes Enabled, Animate, Include this proxy | ||
| + | |||
| + | Proxy Details: Manual Proxy Configuration: Host or IP Address: 127.0.0.1 Port 4445 | ||
| + | |||
| + | Pattern: Regular Expression: <code>^https?://[a-zA-Z0-9.]+\.i2p(:[0-9]{1,5})?(/.*)?$</code> | ||
| + | |||
| + | ==== tor http(s) ==== | ||
| + | |||
| + | General: Set name and color and check boxes Enabled, Animate, Include this proxy | ||
| + | |||
| + | Proxy Details: Manual Proxy Configuration: Host or IP Address: 127.0.0.1 Port 9050 and Check box SOCKS Proxy and SOCKS v4/4a | ||
| + | |||
| + | Patterns: Wildcards: <code>https://*</code> and <code>http://</code> | ||
| + | |||
| + | [[File:Tor1.png|681px|thumb|center]] | ||
| + | |||
| + | ==== default ==== | ||
| + | |||
| + | Leave as is. | ||
| + | |||
| + | === Test === | ||
| + | |||
| + | Set FoxyProxy to ''Use proxies based on their predefined patterns and priorities'' and test. | ||
| + | |||
| + | That’s it. | ||
== Related == | == Related == | ||
| + | * [[Networking concepts]] | ||
| + | * [[Encrypting everything]] | ||
| + | |||
| + | == References == | ||
| + | |||
| + | [[Category:How_To]] | ||
Latest revision as of 08:33, 11 September 2015
Public networks like the internet are very vulnerable to traffic analysis. Packet headers identify the IP addresses of the recipient(s) and the packet routes can rather easily be tracked, see Networking concepts.
Transmissions can be encrypted so that an attacker cannot learn the content of these transmissions, but this still reveals the fact that two parties are communicating. If for example a government official is sending encrypted data to a website of the opposition, and later that site publishes a document that was supposed to be secret, it is pretty clear what happened.
To explain how enhanced communication anonymity can be reached on a linux platform, this page gives an overview of used approaches. The 3 major anonymity networks are Tor/Onionland, I2P/Garlicland and Freenet. If you feel confused on which one is the "best" one to use the answer is simple. Use all three. Each anonymity network is designed for a different purpose. One network alone cannot do what the three can do together. Tor and I2P cannot persist information like Freenet can, Tor and Freenet can't offer the generic transports that I2P provides and Freenet doesn't handle data streaming as well as Tor and I2P. There is also no better proxy system than the Tor network.
To get to the bones and see for yourself, check out the resulting traffic after making changes, for example with wireshark. And to not run into a wall during experimentation (aaaah, nothing works), punch the necessary holes in your firewall. If you adjusted your /etc/sysctl.conf you may want to learn how to use exception options (when available) for commands, or undo some of those changes.
Contents
- 1 Plausible deniability
- 2 SSH tunneling
- 3 Virtual private networks
- 4 Publishing with freenet
- 5 Proxying with tor
- 6 Chaining
- 7 Going underground with i2p
- 8 I2p and tor in iceweasel using foxyproxy patterns
- 9 Related
- 10 References
Plausible deniability
Plausible deniability in networking is about relaying certain types of broadcasts automatically in such a way that the original transmitter of a file is indistinguishable from those who are merely relaying it allows for the person who first transmitted the file to claim that his computer had merely relayed it from elsewhere, and this claim cannot be disproven without a complete decrypted log of all network connections to and from that person's computer, or ...
Plausible deniability has its limits. Recent cryptographic primitives and protocols offer a wide range of features besides confidentiality and integrity. There are many protocols that have more advanced properties such as forward secrecy, deniability or anonymity. In a phrack article a deeper look at deniability in communication (e.g. messaging) protocols appeared. One protocol that claims to offer deniability is OTR. The construction in the article can probably be extended in a quite general way. It shows the limits of deniability, especially in protocols that offer message integrity features (as OTR does). A protocol is constructed that enables each partner in a conversation to cooperate with an observing party, such that he can prove the authenticity of any message that was part of the conversation to the observing party [1].
SSH tunneling
Tunneling with local port forwarding
Imagine wikileaks being blocked using a proxy filter in a university somewhere. A SSH tunnel can be used to bypass this restriction.
Let’s name the machine at the university socially-correct and the home machine as home. The home machine needs to have a public IP and be running a SSH server for this to work. You must have ssh user access on home and socially-incorrect must have access to host:hostport (is not blocked).
$ ssh -L localport:host:hostport user@home -N
where:
- -L: port forwarding parameters
- localport: local port (choose a port that is not in use by other service)
- host: server that has the port (hostport) that you want to forward
- hostport: remote port
- -N: do not execute a remote command (you will not have the shell).
- user: user that has ssh access to the ssh server
- home: the machine/server running the ssh server that will be used for forwarding/tunneling
For example, to create the SSH tunnel execute following from the socially-correct machine:
$ ssh -L 9001:wikileaks.org:80 user@home
+--------------+<-- port 22 -->+--------------+<-- port 80 -->+-----------+
| SSH client |-----------------| SSH server |-----------------| host |
+--------------+ +--------------+ +-----------+
localhost:9001 home wikileaks.org:80
Open a browser and go to http://localhost:9001 to see if the tunnel is working.
Now the SSH client at socially-correct will connect to the SSH server running at home (usually running at port 22) binding port 9001 of socially-correct to listen for local requests thus creating a SSH tunnel between home and socially-correct. At the home end it will create a connection to wikileaks.org at port 80. So socially-correct doesn’t need to know how to connect to wikileaks.org. Only home needs to worry about that. The channel between socially-correct and home will be encrypted while the connection between home and wikileaks.org will be unencrypted.
The home to wikileaks.org connection is only made when the browser makes the request, not at the tunnel setup time.
The SSH man pages say:
-
-L port:host:hostportspecifies that the given port on the local (client) host is to be forwarded to the given host and port on the remote side. This works by allocating a socket to listen to port on the local side, and whenever a connection is made to this port, the connection is forwarded over the secure channel, and a connection is made to host port hostport from the remote machine. Port forwardings can also be specified in the configuration file. Only root can forward privileged ports. IPv6 addresses can be specified with an alternative syntax: port/host/hostport -
-NDo not execute a remote command. This is useful for just forwarding ports (protocol version 2 only).
You can also use local port forwarding to set up a VNC session between socially-correct and your home server. From socially-correct:
$ ssh -L 5900:localhost:5900 user@home
The localhost is relative to the gateway (home in this case), not the machine from where the tunnel is initiated. So this will make a connection to port 5900 of the home computer where the VNC client would be listening in.
Reverse tunneling with remote port forwarding
What if we wish to connect to an internal university website from home? The university firewall is blocking all incoming traffic. We can connect from home to the university internal network so that we can browse the internal site. We can initiate the tunnel from the socially-correct computer behind the firewall. This is possible since only incoming traffic is blocked and outgoing traffic is allowed. The client will now be at the home computer and instead of -L option we use -R which specifies a reverse tunnel is to be created. From socially-correct:
$ ssh -R 9001:internalsite.org:80 user@home
The SSH client at socially-correct will connect to the SSH server running at home creating a SSH channel. The server will bind port 9001 on the home machine to listen for incoming requests that are then routed through the created SSH channel between home and socially-correct. Now it’s possible to browse the internal site by visiting http://localhost:9001 in a web browser on the home machine. The socially-correct machine will then create a connection to internalsite.org and relay back the response to home via the created SSH channel.
Dynamic port forwarding
Dynamic port forwarding allows for configuring one local port for tunnelling data to all remote destinations. This requires the Socks protocol. At the client side of the tunnel a Socks proxy would be created and the application uses the Socks protocol to specify where the traffic should be sent when it leaves the other end of the ssh tunnel. From socially-correct:
$ ssh -D 9001 user@home
SSH will create a Socks proxy listening in for connections at local port 9001 and when receiving a request routes the traffic via the SSH channel created between socially-correct and home. Configure the browser to point to the Socks proxy at port 9001 at localhost.
Virtual private networks
OpenVPN
OpenVPN is free and open source software originally released in 2002. Since then it has become quite popular in the ease it can traverse wireless access points, firewalls, NAT-based routers, and HTTP proxy servers. By using OpenVPN it is possible to use different ports in order to bypass both firewalls and throttling. For more on OpenVPN and other options see networking concepts: VPN.
Working with OpenVPN you will have the ability to work with OpenWRT or DD-WRT and run your local network on a single VPN account. In order to do this you will need to have an OpenVPN account, as well as a router that can be flashed, preferably OpenWRT.
Routed vs bridged VPN
Choose bridging only when:
- the VPN needs to be able to handle non-IP protocols such as IPX
- you are running applications over the VPN which rely on network broadcasts (such as LAN games)
- avoiding setting up a Samba or WINS server for m$ file sharing across the VPN. Better yet, just get rid of the m$ files and machines.
Installing OpenVPN client
If you are using a debian-based distro, you can use a package manager such as apt-get:
$ sudo apt-get install openvpn
It is also possible to install openvpn using the universal ./configure method. First expand the .tar.gz file:
$ tar xfz openvpn-[version].tar.gz
Then cd to the top-level directory, configure and install:
$ sudo ./configure $ sudo make $ make install
You can either use the VPN server you set up yourself, or an existing service. Several autonomous collectives offer services for activists. For bitmask see below. Set it up as described.
Connection failures and DNS leaks
If you simply add a VPN using common instructions, it generally fails open. That means, if the VPN breaks down, because the connection is interrupted, traffic will be sent without the VPN. It's much safer when it fails closed, i.e. when the VPN connection breaks down, the whole internet connection must be down as long as the VPN connection isn't restored.
In addition to VPN connection failures, the other big threat to your anonymity when using a trusted VPN service is that of DNS leaks, which can result in your ISP being able to ‘see’ and monitor your online activity even though you think you are safely protected by an encrypted VPN tunnel.
Using wireshark to check for leaks
This is an example in a debian virtualbox VM, but is also valid in general for other setups.
Virtual machines receive their network address and configuration on the private network from a DHCP server integrated into VirtualBox. The IP address assigned to the virtual machine is on a completely different network than the host (but can be seen with wireshark from the host). As more than one card of a virtual machine can be set up to use NAT, the first card is connected to the private network 10.0.2.0, the second card to the network 10.0.3.0 and so on.
If you haven't installed wireshark yet, see linux security: wireshark for installing and basic usage.
To check if you have DNS leaks, fire up wireshark:
- Start capturing on eth0 and connect to the VPN.
- After capturing either a fixed number of packets, or an amount of data or for a specific time period, go to Statistics -> Endpoints
There should only be one public IP address, namely that of the VPN server that you’re connected to.
Setting DNS nameservers in debian
Resolver libraries look to /etc/resolv.conf for a list of nameservers. In the simplest case, that is the file to edit to set the list of name servers. And various other programs for dynamic configuration will be happy to overwrite your settings:
- The resolvconf program
- The network-manager daemon
- DHCP clients
In most situations, the file to edit is the configuration file for such a program.
Fail:
# Dynamic resolv.conf(5) file for glibc resolver(3) generated by resolvconf(8) # DO NOT EDIT THIS FILE BY HAND -- YOUR CHANGES WILL BE OVERWRITTEN
In case the network you hook into uses DHCP and you set your DNS nameservers (in debian) manually in /etc/resolv.conf, any change will be lost as it gets overwritten next time something triggers resolvconf. And adding nameservers after a loopback in interfaces doesn’t work either.
resolvconf is a set of script and hooks managing DNS resolution using DHCP client hooks, a network manager plugin and /etc/network/interfaces to generate a list of nameservers and domain to put in /etc/resolv.conf
The /etc/resolvconf/resolv.conf.d directory (probably) contains base, head, original and tail files in resolv.conf format:
- base: used when no other data can be found
- head: for the header of resolv.conf, can be used to ensure a DNS server is always the first one in the list
- original: backup of your resolv.conf at the time of resolvconf installation
- tail: appended at the end of the resulting resolv.conf
Open the head file with your favorite editor for it (geany, vi, vim, nano) as root (sudo, su or root terminal). The head file contains the same warning as above … but in this case it is there so that when the resolv files are constructed, the warning will ultimately work its way into the resulting resolv.conf file.
Add (or replace) the nameservers you picked from for example, the opennic project or the wikileaks alternative DNS list:
nameserver nnn.nnn.nnn.nnn nameserver nnn.nnn.nnn.nnn
Then update:
$ sudo resolvconf -u
And test by viewing the results in /etc/resolv.conf. You can also create /etc/resolv.conf.tail, but do check because only the first two are used.
Punching holes in ufw for a VPN
To forcibly prevent DNS leaks use a firewall. ufw can be set up as a fail safe mechanism (aka kill switch).
Install ufw if not already installed.
Set all traffic to deny:
$ sudo ufw default deny outgoing $ sudo ufw default deny incoming
Permit OpenVPN traffic (if using OpenVPN adapter is probably tun0 but check)
$ sudo ufw allow out on tun0 from any to any
For added security you may want to keep incoming traffic disabled but if desired or required then allow it:
$ sudo ufw allow in on tun0 from any to any
With this rule all non VPN traffic (and subsequently DNS requests not routed though VPN) will be blocked.
But, this set up requires that you disable the firewall to connect to the VPN and then enable it once connection is made. To allow establishment of a connection to the VPN server even when the firewall is enabled:
$ sudo ufw allow out from any to [VPN server IP address]
Add multiple rules for all VPN servers you will be using. If you want more strict rules and better security then only allow desired ports on tun0.
Using the VPNfirewall script
The VPNfirewall script by Adrelanos:
- Forbids outgoing traffic after the VPN software broke down for some reason.
- Has tight firewall rules, using iptables policy drop.
- Only tested with OpenVPN. Should work with other VPN clients such as PPTP in theory, you should test if it does what it claims anyway.
- Only tested on Debian Wheezy and Whonix. Should work on any other Linux distribution in theory, you should test if it does what it claims.
- Open Source / Free Software
More here, including how to install it: https://github.com/adrelanos/VPN-Firewall
Bitmask
Bitmask is an open source application to provide easy and secure encrypted communication. You can choose among several different service providers or start your own. Currently, Bitmask supports encrypted internet (VPN) with encrypted email coming soon. https://bitmask.net/
Publishing with freenet
Freenet uses UDP and is the "oldest" of the 3 networks. Freenet is an anonymous data publishing network and very different from Tor and I2P. Freenet is much higher latency and focuses more on friend to friend interactions with often military grade security. It is slow and very resource intensive.
Freenet is a tool for bypassing totalitarian censorship where people would be killed for publishing certain content. It is not for casual browsing. https://freenetproject.org/
Proxying with tor
Tor is an anonymous internet proxy using onion routing. In an onion network, messages are encapsulated in layers of encryption, analogous to layers of the vegetable onion. The encrypted data is transmitted through a series of network nodes called onion routers, each of which "peels" away a single layer, uncovering the data's next destination. When the final layer is decrypted, the message arrives at its destination. The sender is thought to remain anonymous because each intermediary knows only the location of the immediately preceding and following nodes. Connections with Tor aren't dynamic like I2P tunnels are, Tor circuits persist until closed. This can reduce anonymity. There is no support for UDP.
The best use for Tor is anonymous proxying to the regular internet. It is the most sophisticated and robust system for proxying currently devised. And despite Tor being a powerful tool, it is possible to distinguish Tor traffic from normal traffic, and it is possible to perform correlation-based attacks to de-anonymise our use of it.
Browser bundle
The Firefox-based Tor Browser Bundle integrates the Tor network's enhanced privacy and security. It includes the Vidalia network connection utility. It's installation is easy and it works out of the box. https://www.torproject.org/projects/torbrowser.html.en
Liberté linux, tails, whonix, freepto
There are also a few distro's and live CD/DVD's focused on anonymity that are based on use of tor.
Really, comparisons are useless, except for making it easier to choose which one suits a specific purpose and environment best.
These tables are a year old, and need revisiting, checking and updating. Also, Freepto will need to be tried out further and added.
General
| Liberté linux | Tails | Whonix | Freepto |
|---|---|---|---|
| Liberté Linux[2] is a secure[3], reliable, lightweight and easy to use [4] Gentoo-based LiveUSB/SD/CD Linux distribution with the primary purpose of enabling anyone to communicate safely and covertly in hostile environments [5]. Whether you are a privacy advocate, a dissident, or a sleeper agent, you are equally likely to find Liberté Linux useful as a mission-critical communication aid. | Tails [6] is a live operating system [7], that you can start on almost any computer from a DVD, USB stick, or SD card. It aims at preserving your privacy and anonymity, and helps you to use the Internet anonymously and circumvent censorship; leave no trace on the computer you are using unless you ask it explicitly and use state-of-the-art cryptographic tools to encrypt your files, emails and instant messaging. | Whonix [8] is an Anonymous Operating System. It hides your IP/location and uses Tor to anonymize your data traffic. This means that neither the contacted server, nor any eavesdropper on your connections, nor the operators of the Tor network themselves can realize which webservice you use. | Freepto [9] is a live operating system aiming to be a powerful tool for activists, journalists, whistleblowers, and people that want to protect their privacy. Runs entirely on a USB key. Uses the Metadata Anonymisation Toolkit [10]. |
| Hardened Gentoo kernel [11], which includes all grsecurity/PaX security enhancements [12]. | Debian based [13] | Debian based | Debian based |
| HDD, bootable media, virtualized environments (but was developed for USB) | Bootable media, virtualized environments (but was developed for LiveCD) | HDD (but such an install misses the point of isolation via VirtualBox), virtualized environments | Bootable media |
| Relatively young | Well tested and peer reviewed | Relatively young | Young |
| Lightweight but do not be put off by its small image size — Liberté Linux is a fully capable distribution with HTML5 video support in the browser, file managers and chat plugins, audio players, a multitude of multilingual fonts, full application interface and keyboard localization, and much more. | Balance between functionality and available space and security | An anonymous general purpose operating system | An anonymous general purpose operating system |
| Pseudonymous dev | Non-anonymous dev team | Non-anonymous dev | Under development by AvANa[14], the resident hacktivist collective of Forte Prenestino[15], one of the oldest and most famous social centrer (squat) in Italy. |
Memory matters
| Liberté Linux | Tails | Whonix | Freepto |
|---|---|---|---|
| Download size is 200+ MB | Download size is 800+ MB | You need to download VirtualBox and both Gateway and Workstation virtual machine images. Both VMs together are currently almost 2 GB | Download size is ~ 1.0 GB |
| Installed 220+ MB | Installed 1500+ MB | VirtualBox will need about 30 MB of hard disk space, the VM’s 2GB, plus the virtual disk sizes set in the VM’s | |
| Can run from USB stick with other files. Remaining space can be used even in windows. | Uses all space on the usb stick. Remaining space is wasted or made persistent. | Virtual disks on hosts | |
persistent is an encrypted file on USB. It can be viewed in Windows with FreeOTFE. You can create your own encrypted containers from command line with otfe |
persistent is a partition on USB space. Cannot be viewed in Windows, meaning, we don’t know how to view it. Yet. | Full persistence. You can add full disk encryption to host, and use file encryption in guest to your liking. | |
| Runs with 192 MB RAM | Needs a lot of RAM | Setting the Virtual Machine RAM to use less than 512MB will boot the workstation into console mode |
User friendliness
| Liberté Linux | Tails | Whonix | Freepto |
|---|---|---|---|
| Runs on older PCs. | Is a headache on older PCs or on PCs with small memory. And with every new version shipped older and newer PCs become too old. | Whonix has higher hardware requirements, and therefore more space to implement features. | |
| Upgrading by overwriting files (even from windows). Installing software on Liberte is not for newbies: there is no way to install software into its root tree — both due to lack of toolchain and portage, and due to read-only mode of most of the filesystem. The only way of adding software is building a custom image, or using portable binaries (provided that their required libraries are available). See making our own LiveCD/DVD images. | Upgrading and installing additional software can be done from bootable medium. | Upgrading and installing additional software can be done from guest using Apper or Synaptic package. |
Applications
| Liberté Linux | Tails | Whonix | Freepto |
|---|---|---|---|
| Browser: Epiphany plus patches. Opens a menu page. | Browser: Iceweasel. Default opening page is set to “check.torproject.org” | Browser: Tor Browser with extensions | |
| Password Management: Figaro’s Password Manager | Password Management: KeePassX | Choice | |
| Pidgin (with OTR) is “empty” by default | Pidgin client comes pre-configured with an OFTC account over SSL and a nickserv | Choice of chat clients | |
| Claws is pre-configured with a “cables” account (on pendrive only). Cables is a p2p message system on a Claws email GUI. Both sender and receiver need to “see” each other to exchange “emails”. Can cost up to half an hour before your Cables node is discoverable by the other party | Claws installs “empty” | Mozilla Thunderbird with TorBirdy | |
| XChat (with SASL) | XChat | XChat in Whonix has been hardened according to TorifyHOWTO/XChat [16] |
Security
| Liberté Linux | Tails | Whonix | Freepto |
|---|---|---|---|
| When using mobile phone connectivity, such as 3G or GSM, the identifier of your SIM card (IMSI) and the serial number of your phone (IMEI) are always revealed to the mobile phone operator. [17] | Most dangerous leaks are protected and many default applications are already configured, not to leak[18] | ||
| Mac Changer: tries to perform a mac address change at startup. | The uniqueness of MAC addresses introduce two types of potential issues for Tails users, in particular if the MAC address can be linked to the user's identity. Spoofing the MAC address is the natural solution. Unfortunately, in some cases MAC spoofing may cause network connection issues or even raise alarms; care should be taken to prevent MAC spoofing in such situations. [19] | There is no support for MAC address use in this domain. This is still an open research problem. [20] | |
| Amnesic | Amnesic | Not amnesic | |
| The only way to become root is by logging out during first 2 minutes after boot, then press Alt-F2, then run passwd. 😀 | In case Tails gets rooted, the adversary can bypass the firewall and get the user’s real IP. | The Workstation is the place where the browser, IRC client and so on is running. The Gateway is the place where Tor and the firewall is running. The Whonix-Workstation is unaware of its external IP. | |
| The Tails developers have plans to implement persistent entry guards [21]. That ticket also contains additional extra information, such as a link to a discussion about a missing feature: Location-aware persistent guards [22]. In an ideal world, users could enter a pin/token/password to choose various sets of entry guards [23] | You could consider to always use non-persistent entry guards. In most cases, this is something to avoid because persistent entry guards is a security feature as explained in the introduction. A more secure, but more time expensive approach would be Alternating Bridges. [24] | ||
| NTP is the only application that potentially must communicate in the clear — to a known server pool. NTP is not necessary for correct operation of Liberté, and it is currently turned off to prevent timestamp-based fingerprinting and MIM DoS attacks. Torified HTP adjusts the time very reliably — albeit with less precision. In general, Tor requires a correct computer clock to start up, but in Liberté this problem is circumvented using a consensus-based time estimate. | Uses consensus (waits up to 150 seconds twice, restarting Tor in between), checks authority certificate, sets the system time to the valid-after of the unverified consensus Tor fetched, which will guarantee that the certificate and consensus are all valid. Then restarts Tor (since it behaves badly with time jumps during the early bootstrap stages) and waits until it accepts the consensus and finishes the bootstrap. HTP is then through Tor to get a more correct system time. [25] | Whonix leaves the host's system clock or time synchronization mechanism untouched.
Whonix-Gateway and Whonix-Workstation are based on VirtualBox and therefore have their own virtual hardware system clocks. Most VirtualBox time synchronization features get disabled by Whonix. [26] || | |
| Until an audit of the bundled network applications is done, information leakages at the protocol level should be considered as − at the very least − possible [27] | Whonix security in real world [28] | ||
| We want to enable IsolateDestAddr and IsolateDestPort for the SocksPort used by most applications, unless we tell them otherwise.[29] | Whonix implements protection against identity correlation through circuit sharing, however, for better privacy, you are still advised to understand a bit of the technical background. [30] | ||
| To make it difficult to distinguish Tails users, Tor Browser in Tails tries to provide the same information as Tor Browser on other operating systems in order to have similar fingerprints. [31] | To make it difficult to distinguish Whonix users from Browser bundle users, Whonix includes the Browser bundle and therefore should provide the same information as the Browser bundle in order to have similar fingerprints. [32] | ||
| All volatile memory is thoroughly erased upon shutdown in order to prevent cold boot attacks — whether an orderly shutdown, or an immediate one due to abrupt removal of the boot media. | To prevent cold boot attacks, the data in RAM is overwritten by random data when shutting down Tails. This erases all traces from your session on that computer. [33] | No protection from cold boot attacks |
Tor on host
If you also wish to use other applications than browsing and/or you wish to chain, install tor on your box.
Installing tor and privoxy
For installing tor follow the instructions give by the tor project https://www.torproject.org/docs/debian.html.en#ubuntu
For installing privoxy http://www.privoxy.org/user-manual/installation.html
Configuring privoxy
When using socks5 on port %d, your application is giving Tor only an IP address. Applications that do DNS resolves themselves may leak information. So using Socks4A instead is a good idea. More on that here https://www.torproject.org/docs/faq#WarningsAboutSOCKSandDNSInformationLeaks.
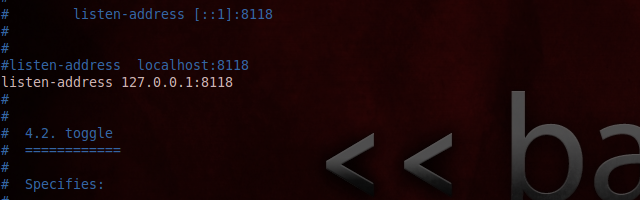
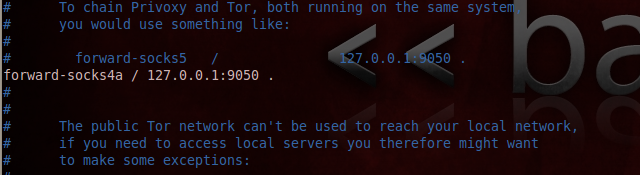
Open /etc/privoxy/config, check that the listen address is 127.0.0.1:8118, and set forward in privoxy to tor with forward-socks4a / 127.0.0.1:9050 . (Do NOT forget that point at the end). Save.
Temporarily set your system wide network settings or the network settings in your browser to Manual Proxy configuration with Host or IP Adress 127.0.0.1 and port 9050. Check with http://check.torproject.org that it works. If it doesn’t work, maybe this faq helps https://www.torproject.org/docs/faq#DoesntWork
Undo the network settings: Set both, system wide and browser network settings to automatic, configure clients with IP address 127.0.0.1 and chosen port(s), and set up multiple circuits for separating streams. Whonix https://www.whonix.org/ and Tails are great to learn from.
Transparently routing traffic through tor
Requires iptables:
- https://trac.torproject.org/projects/tor/wiki/doc/TransparentProxy
- https://help.ubuntu.com/community/TorDedicatedUser
Configuring browser
With IE, Opera and Safari there are too many ways that our privacy can be breached, and because of their closed design it is really hard to do anything about such privacy problems, hence the focus on Firefox and Konquerer.
In Firefox go to Edit —> Preferences —> Advanced tab —> Connection (Click Settings … button).
For an example of setting proxies (and switching between proxies) see foxyproxy.
Configuring xchat
Torbirdy for icedove
Configuring console-based applications with proxychains
For using Tor with console based “clients”, applications that do not have any settings for adding proxy addresses, add the command “proxychains” in front of your commands. We can also add elinks, Elinks, a ‘text-browser’ that makes it possible to browse the internet without displaying images (Images and other media like pdf’s can optionally be displayed).
Install proxychains and elinks:
$ apt-get install proxychains elinks
Open /etc/proxychains.conf and check the following line exists (if not, add it): socks4 127.0.0.1 9050
Check that it works by running the following commands and comparing results:
$ proxychains elinks cmyip.com
and
$ elinks cmyip.com
If wurks, you can for example anonymously run nmap anysite.com:
$ proxychains nmap [anysite.com]
Chaining
Going underground with i2p
I2P is a Distributed Peer to Peer Anonymous Network Layer that is strictly message-based (like IP), but there is a library available to allow reliable streaming communication on top of it (similar to TCP, although from version 0.6 there is a new UDP-based SSU transport). It allows you to send data between computers running I2P anonymously with multilayer end to end encryption. The name I2P derived from Invisible IRC Project (IIP) which was one of FreeNet's sister projects. I2P focuses on exclusively internal communication and not proxying to the regular internet. I2P uses garlic routing which involves clumping packets together into bigger packets. The combination of garlic routing, multilayer encryption -even the end points ("destinations") are cryptographic identifiers- and random padding on packets makes analysis of the content and detection of the origin of I2P traffic by third-party observers highly impractical if not nearly impossible.
The best use for I2P is for peer to peer file sharing and a replacement for the regular internet in the event that it gets bad enough to warrant such action.
Installing
Install according to the guides on this page: https://geti2p.net/en/download/debian
Starting up automagically
Add i2prouter start to your start up applications, and reboot. You can also set up i2p to boot before you even login:
$ sudo dpkg-reconfigure i2p
In which case you may have to do some port forwarding.
Set browser to always use Private Browsing. You can still use bookmarks to remember your most used pages. Reboot and wait for the i2p router console to come up.
ufw rules
I2p and tor in iceweasel using foxyproxy patterns
Prelims
- Install tor and i2p
- Add FoxyProxy plugin/extension to Iceweasel/Firefox http://getfoxyproxy.org/
Patterns
I made use of a rainbow of colors that tell me what I am using while I browse, ending in red (default proxy), warning me I am naked. Note that order matters. For more on regular expressions see Kinky linux command-line: Regular expressions.
i2p router console
General: Set name and color and check boxes Enabled, Animate, Include this proxy
Proxy Details: Direct internet connection (no proxy)
Pattern: Wildcard: http://127.0.0.1:7657/*
local eepsite
General: Set name and color and check boxes Enabled, Animate, Include this proxy
Proxy Details: Direct internet connection (no proxy)
Pattern: Wildcard: http://127.0.0.1:7658/*
i2p eepsites http
General: Set name and color and check boxes Enabled, Animate, Include this proxy
Proxy Details: Manual Proxy Configuration: Host or IP Address: 127.0.0.1 Port 4444
Pattern: Regular Expression: ^http://[-a-zA-Z0-9.]+\.i2p(:[0-9]{1,5})?(/.*)?$
You will get this message. Just click Yes.
i2p eepsites https
General: Set name and color and check boxes Enabled, Animate, Include this proxy
Proxy Details: Manual Proxy Configuration: Host or IP Address: 127.0.0.1 Port 4445
Pattern: Regular Expression: ^https?://[a-zA-Z0-9.]+\.i2p(:[0-9]{1,5})?(/.*)?$
tor http(s)
General: Set name and color and check boxes Enabled, Animate, Include this proxy
Proxy Details: Manual Proxy Configuration: Host or IP Address: 127.0.0.1 Port 9050 and Check box SOCKS Proxy and SOCKS v4/4a
Patterns: Wildcards: https://* and http://
default
Leave as is.
Test
Set FoxyProxy to Use proxies based on their predefined patterns and priorities and test.
That’s it.
Related
References
- ↑ Secure Function Evaluation vs. Deniability in OTR and similar protocols http://phrack.org/issues/68/14.html#article
- ↑ Liberté Linux http://dee.su/liberte
- ↑ Liberté security http://dee.su/liberte-security
- ↑ Liberté Linux Documentation http://dee.su/liberte-documentation
- ↑ Liberté Linux motivation http://dee.su/liberte-motivation
- ↑ Tails https://tails.boum.org
- ↑ Wikipedia LiveUSB https://en.wikipedia.org/wiki/Live%5FUSB
- ↑ Whonix https://www.whonix.org/wiki/Main_Page
- ↑ Freepto http://avana.forteprenestino.net/freepto/
- ↑ Metadata Anonymisation Toolkit https://mat.boum.org
- ↑ Hardened Gentoo kernel http://www.gentoo.org/proj/en/hardened/
- ↑ grsecurity/PaX http://grsecurity.net/
- ↑ Debian http://www.debian.org/
- ↑ AvANa http://avana.forteprenestino.net/
- ↑ Forte Prenestino http://www.forteprenestino.net/
- ↑ TorifyHOWTO/XChat https://trac.torproject.org/projects/tor/wiki/doc/TorifyHOWTO/XChat
- ↑ Are hardware serial numbers hidden in TAILS? https://tails.boum.org/doc/first_steps/startup_options/mac_spoofing/index.en.html
- ↑ Protocol-Leak-Protection and Fingerprinting-Protection https://www.whonix.org/wiki/Protocol-Leak-Protection_and_Fingerprinting-Protection
- ↑ Mac Changer: MAC address anonymization is under development https://tails.boum.org/contribute/design/MAC_address/
- ↑ Mac Address https://www.whonix.org/wiki/Pre_Install_Advice#MAC_Address
- ↑ Persistence preset: Tor state https://labs.riseup.net/code/issues/5462
- ↑ [tor-talk] Location-aware persistent guards https://lists.torproject.org/pipermail/tor-talk/2012-October/025975.html
- ↑ Support more stable guards for live CDs https://trac.torproject.org/projects/tor/ticket/2653
- ↑ Non-Persistent Entry Guards https://www.whonix.org/wiki/Tor#Non-Persistent_Entry_Guards
- ↑ Tails Design: Time syncing https://tails.boum.org/contribute/design/Time_syncing/
- ↑ Whonix Design: TimeSync https://www.whonix.org/wiki/Dev/TimeSync
- ↑ Applications audit https://labs.riseup.net/code/issues/5769
- ↑ Whonix security in real world https://www.whonix.org/wiki/Security_in_Real_World
- ↑ Tails separate Tor streams https://labs.riseup.net/code/issues/5334
- ↑ Stream Isolation https://www.whonix.org/wiki/Stream_Isolation
- ↑ Tails Fingerprint Page https://tails.boum.org/doc/about/fingerprint/index.en.html
- ↑ Whonix Fingerprint Page https://www.whonix.org/wiki/Fingerprint
- ↑ Protection against cold boot attacks https://tails.boum.org/doc/advanced_topics/cold_boot_attacks/index.en.html