Networking concepts
From Gender and Tech Resources
bla
Contents
- 1 Network topology
- 2 Hardware connections
- 3 TCP/IP ports and addresses
- 4 Network protocol levels
- 5 Data link layer
- 6 TCP/IP network protocols
- 7 Repeaters, bridges, routers
- 8 ARP and RARP address translation
- 9 Basic addressing
- 10 IP (network)
- 11 TCP (transport)
- 12 UDP (transport)
- 13 ICMP
- 14 Applications
Network topology
A network consists of multiple digital devices connected using some type of interface, each having one or more interface devices such as a Network Interface Card (NIC) and/or a serial device for PPP networking. Each digital device is supported by network software that provides server and/or client functionality.
We can make distinctions in type according to centralisation vs distribution:
- In a server based network, some devices are set up to be primary providers of services. These devices are called servers and the devices that request and use the service are called clients.
- In a peer-to-peer network, various devices on the network can act both as clients and servers. Like a network of switchers. :D
The network topology describes the method used to do the physical wiring of the network. The main ones are:
- Bus networks (not to be confused with the system bus of a computer) use a common backbone to connect all devices. Both ends of the network must be terminated with a terminator. A barrel connector can be used to extend it. A device wanting to communicate with another device on the network sends a broadcast message onto the wire that all other devices see, but only the intended recipient actually accepts and processes the message. Bus networks are limited in the number of devices it can serve due to the broadcast traffic it generates.
- Ring networks connecting from one to another in a ring. Every device has exactly two neighbors. A data token is used to grant permission for each computer to communicate. All messages travel through a ring in the same direction, either "clockwise" or "counterclockwise". A failure in any cable or device breaks the loop and can take down the entire network, so there are also rings that have doubled up on networking hardware and information travels both "clockwise" and "counterclockwise".
- Star networks using a central connection point called a "hub node", a network hub, switch or router, that controls the network communications. Most home networks are of this type. Star networks are limited in number of hub connection points.
- Tree networks join multiple star topologies together onto a bus. In its simplest form, only hub devices connect directly to the tree bus, and each hub functions as the root of a tree of devices.
- Mesh networks use routes. Unlike the previous topologies, messages sent on a mesh network can take any of several possible paths from source to destination. Most prominent example is the internet.
Hardware connections
- A Network Interface Card (NIC) is a hardware device that allows a computer to connect to a network.
- Each network interface card (NIC) has a built in hardware address programmed by its manufacturer. This is a 48 bit address and should be unique for each card. This address is called a media access control (MAC) address.
- You can connect two digital devices (computers) together with a cross-over cable between their network cards, not a straight network jumper cable (otherwise the transmit port would be sending to the transmit port on the other side).
- A network hub is a hardware device to connect network devices together. The devices will all be on the same network and/or subnet. All network traffic is shared and can be sniffed by any other node connected to the same hub.
- Uplink does not have a crossover connection and is designed to fit into a crossover connection on the next hub. This way you can keep linking hubs to put more computers on a network. Because each hub introduces some delay onto the network signals, there is a limit to the number of hubs you can sequentially link. Also the computers that are connected to the two hubs are on the same network and can talk to each other. All network traffic including all broadcasts is passed through the hubs.
- A network switch is like a hub but creates a private link between any two connected nodes when a network connection is established. This reduces the amount of network collisions and thus improves speed. Broadcast messages are still sent to all nodes.
- If you have a machine (device, computer) with two network cards, eth0, connected to an outbound hub, and eth1, connected to another hub that only connects to local machines, and it is not configured as router or bridge, the two networks are considered separated. If no other machines on the network that the eth0 card is connected to, is an outbound device, all devices in that network are dependent.
TCP/IP ports and addresses
The part of the network that does the job of transporting and managing the data across the "normal" internet is called TCP/IP which stands for Transmission Control Protocol (TCP) and Internet Protocol (IP). The IP layer requires a 4 (IPv4) or 6 (IPv6) byte address to be assigned to each network interface card on each computer. This can be done automatically using network software such as Dynamic Host Configuration Protocol (DHCP) or by manually entering static addresses.
Port numbers
The TCP layer requires what is called a port number to be assigned to each message. This way it can determine the type of service being provided. These are not ports that are used for serial and parallel devices or for computer hardware control, but reference numbers used to define a service (RFC 6335).
Addresses
Addresses are used to locate computers, almost like a house address. Each IP address is written in what is called dotted decimal notation. This means there are four numbers, each separated by a dot. Each number represents a one byte value with a possible range of 0-255.
Network protocol levels
Protocols are sets of standards that define all operations within a network and how devices outside the network can interact with the network. Protocols define everything: basic networking data structures, higher level application programs, services and utilities.
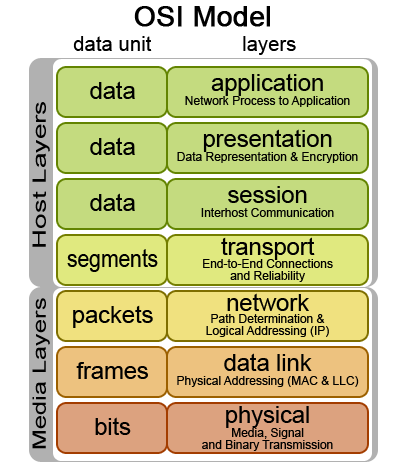
The International Standards Organization (ISO) has defined the Open Systems Interconnection (OSI) model for current networking protocols, commonly referred to as the ISO/OSI model (ISO standard 7498-1). It is a hierarchical structure of seven layers that defines the requirements for communications between two computers. It was conceived to allow interoperability across the various platforms offered by vendors. The model allows all network elements to operate together, regardless of who built them. By the late 1980's, ISO was recommending the implementation of the OSI model as a networking standard. By that time, TCP/IP had been in use for years. TCP/IP was fundamental to ARPANET and the other networks that evolved into the internet. For differences between TCP/IP and ARPANET, see RFC 871. Only a subset of the whole OSI model is used today.
RFCs
Protocols are outlined in Request for Comments (RFCs). The RFCs central to the TCP/IP protocol:
- RFC 1122 - Defines host requirements of the TCP/IP suite of protocols covering the link, network (IP), and transport (TCP, UDP) layers.
- RFC 1123 - The companion RFC to 1122 covering requirements for internet hosts at the application layer
- RFC 1812 - Defines requirements for internet gateways which are IPv4 routers
ISO/OSI model
7. The Application layer provides a user interface by interacting with the running application. Examples of application layer protocols are Telnet, File Transfer Protocol (FTP), Simple Mail Transfer Protocol (SMTP) and Hypertext Transfer Protocol (HTTP).
6. The Presentation layer transforms data it receives from and passes on to the Application layer and Session layer. MIME encoding, data compression, data encryption and similar manipulations of the presentation are done at this layer. Examples: converting an EBCDIC-coded text file to an ASCII-coded file or from a .wav to .mp3 file, or serializing objects and other data structures into and out of XML. This layer makes the type of data transparent to the layers around it.
5. The Session layer establishes, manages and terminates the connections between local and remote applications. The OSI model made this layer responsible for "graceful close" of sessions (a property of TCP), and session checkpointing and recovery (usually not used in the internet protocol suite). It provides for duplex or half-duplex operation, dialog control (who transmits next), token management (who is allowed to attempt a critical action next) and establishes checkpointing of long transactions so they can continue after a crash, adjournment, termination, and restart procedures.
- Full Duplex allows the simultaneous sending and receiving of packets.
- Half Duplex allows the sending and receiving of packets in one direction at a time only.
4. The Transport layer provides end-to-end delivery of data between two nodes and is responsible for the delivery of a message from one process to another. It converts messages into Transmission Control Protocol (TCP), User Datagram Protocol (UDP), Stream Control Transmission Protocol (SCTP), etc. Some protocols are state and connection oriented, allowing the transport layer to keep track of the packets and retransmit those that fail: It divides data into different segments before transmitting it. On receipt of these segments, the data is reassembled and forwarded to the next layer. If the data is lost in transmission or has errors, then this layer recovers the lost data and transmits the same.
3. The Network layer translates the network address into a physical MAC address. It performs network routing, flow control, segmentation/desegmentation, and error control functions. The best known example of a layer 3 protocol is the Internet Protocol (IP).
2. The Data Link layer is responsible for moving frames from one hop (node) to the next. The main function of this layer is to convert the data packets received from the upper layer(s) into frames, to establish a logical link between the nodes, and to transmit the frames sequentially. The addressing scheme is physical as MAC addresses are hard-coded into network cards at the time of their manufacture. The best known example is data transfer method (802x ethernet). IEEE divided this layer into the two following sublayers:
- Logical Link Control (LLC) maintains the link between two computers by establishing Service Access Points (SAPs) which are a series of interface points. See IEEE 802.2.
- Media Access Control (MAC) is used to coordinate the sending of data between computers. See the IEEE 802.3, 4, 5, and 12 standards.
1. The Physical layer coordinates the functions required to transmit a bit stream over a physical medium. It defines all the electrical and physical specifications for devices. This includes layout of pins, voltages, cable specifications, etc. Hubs, repeaters and network adapters are physical-layer devices. Popular protocols at this layer are Fast Ethernet, ATM, RS232, etc. The major functions and services performed by the physical layer are:
- Establishment and termination of a connection to a device.
- Participation in the process whereby resources are effectively shared among multiple users.
- Modulation, or conversion between the representation of digital data in user equipment and the corresponding signals transmitted over a channel. These are signals operating over the physical cabling or over a radio link.
TCP/IP model
4. The Application layer includes all the higher-level protocols such as TELNET, FTP, DNS SMTP, SSH, etc. The TCP/IP model has no session or presentation layer. Its functionalities are folded into its application layer, directly on top of the transport layer.
3. The Transport layer provides datagram services to the Application layer. This layer allows host and destination devices to communicate with each other for exchanging messages, irrespective of the underlying network type. Error control, congestion control, flow control, etc., are handled by the transport layer. The protocols used are the Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP gives a reliable, end-to-end, connection-oriented data transfer, while UDP provides unreliable, connectionless data transfers.
2. The Internet layer (alias Network layer) routes data to its destination. Data received by the link layer is made into data packets (IP datagrams), containing source and the destination IP address or logical address. These packets are sent and delivered independently (unordered). Protocols at this layer are Internet Protocol (IP), Internet Control Message Protocol (ICMP), etc.
1. The Network Interface layer combines OSI's Physical and Data Link layers.
Data link layer
The IEEE 802 standards define the two lowest levels of the seven layer network model and primarily deal with the control of access to the network media [1]. The network media is the physical means of carrying the data such as network cable. The control of access to the media is called media access control (MAC).
Network access methods
All clients talking at once doesn't work. What ways have been developed sofar to avoid this?
- Contention
- Carrier-Sense Multiple Access with Collision Detection (CSMA/CD) used by ethernet
- Carrier-Sense Multiple Access with Collision Avoidance (CSMA/CA)
- Token Passing - A token is passed from one computer to another, which provides transmission permission.
- Demand Priority - Describes a method where intelligent hubs control data transmission. A computer will send a demand signal to the hub indicating that it wants to transmit. The hub sill respond with an acknowledgement that will allow the computer to transmit. The hub will allow computers to transmit in turn.
- Polling - A central controller, also called the primary device will poll computers, called secondary devices, to find out if they have data to transmit. Of so the central controller will allow them to transmit for a limited time, then the next device is polled.
Ethernet uses CSMA/CD, a method that allows network stations to transmit any time they want. Network stations sense the network line and detect if another station has transmitted at the same time they did. If such a collision happened, the stations involved will retransmit at a later, randomly set time in hopes of avoiding another collision.
Data encapsulation
1. One computer requests to send data to another over a network.
2. The data message flows through the Application layer by using a TCP or UDP port to pass onto the Internet layer. The Transport layer may have one of two names, segment or datagram. If the TCP protocol is being used, it is called a segment. If the UDP protocol is being used, it is called a datagram.
3. The data segment obtains logical addressing at the Internet layer via the IP protocol, and the data is then encapsulated into a datagram. The requirements for IP to link layer encapsulation for hosts on a Ethernet network are:
- All hosts must be able to send and receive packets defined by RFC 894.
- All hosts should be able to receive a mix of packets defined by RFC 894 and RFC 1042.
- All hosts may be able to send RFC 1042 defined packets.
Hosts that support both must provide a means to configure the type of packet sent and the default must be packets defined by RFC 894.
4. The datagram enters the Network Access layer, where software will interface with the physical network. A data frame encapsulates the datagram for entry onto the physical network. At the end of the process, the frame is converted to a stream of bits that is then transmitted to the receiving computer.
5. The receiving computer removes the frame, and passes the packet onto the Internet layer. The Internet layer will then remove the header information and send the data to the Transport layer. Likewise, the Transport layer removes header information and passes data to the final layer. At this final layer the data is whole again, and can be read by the receiving computer if no errors are present.
Encapsulation formats
Ethernet (RFC 894) message format:
- 6 bytes for destination address
- 6 bytes for source address.
- 2 bytes of message type indicating the type of data being sent
- 46 to 1500 bytes of data.
- 4 bytes for cyclic redundancy check (CRC) information
IEEE 802 (RFC 1042) message format:
- IEEE 802.3 Media Access Control section used to coordinate the sending of data between computers:
- 6 bytes for destination address
- 6 bytes for source address
- 2 bytes for length - The number of bytes that follow not including the CRC.
- IEEE 802.2 Logical Link control establishes service access points (SAPs) between computers:
- 1 byte destination service access point (DSAP)
- 1 byte source service access point (SSAP)
- 1 byte for control
- Sub Network Access Protocol (SNAP):
- 3 bytes for org code.
- 2 bytes for message type which indicates the type of data being sent
- 38 to 1492 bytes of data
- 4 bytes for cyclic redundancy check (CRC) information
Trailor encapsulation
This link layer encapsulation is described in RFC 1122 and RFC 892. It is not used very often today and may be very interesting for some further experimentation with.
TCP/IP network protocols
TDP/IP includes a wide range of protocols which are used for a variety of purposes on the network. The set of protocols that are a part of TCP/IP is called the TCP/IP protocol stack or the TCP/IP suite of protocols https://en.wikipedia.org/wiki/Internet_protocol_suite.
| ISO/OSI | TCP/IP | TCP/IP protocol examples | Notes |
|---|---|---|---|
| Application, session, presentation | Application | NFS, NIS, DNS, RPC, LDAP, telnet, ftp, rlogin, rsh, rcp, RIP, RDISC, SNMP, and others | FTP, TFTP, SMTP, Telnet, NFS, ping, rlogin provide direct services to the user. DNS provides address to name translation for locations and network cards. RPC allows remote computer to perform functions on other computers. RARP, BOOTP, DHCP, IGMP, SNMP,RIP, OSPF, BGP, and CIDR enhances network management and increases functionality. |
| Transport | Transport | TCP, UDP, SCTP | Controls the management of service between computers. Based on values in TCP and UDP messages a server knows what service is being requested. |
| Network | Internet | IPv4, IPv6, ARP, ICMP | ARP communicates between layers to allow one layer to get information to support another layer. This includes broadcasting. IP and ICMP manage movement of messages and report errors (including routing). |
| Data link | Data link | PPP, IEEE 802.2, HDLC, DSL, Frames, Network Switching, MAC address | Allows messages to be packaged and sent between physical locations. |
| Physical | Physical network | Ethernet (IEEE 802.3), Token Ring, RS-232, FDDI, and others | Allows messages to be packaged and sent between physical locations. |
- Hypertext Transfer Protocol (HTTP) is the protocol that facilitates transfer of data. Typically, data is transferred in the form of pages, or HTML markup. HTTP operates on TCP port 80.
- Secure HTTP (HTTPS) uses TCP port 443 to securely transfer HTTP data via SSL, or Secure Socket Layer. TLS is the newer SSL.
- File Transfer Protocol (FTP) operates on TCP ports 20 (data)/21(transmission control). It is used in simple file transfers from one node to another without any security (transferred in cleartext). Secure (SFTP) is a version of FTP that uses SSH to transfer data securely, using whichever port SSH uses (usually 22).
- Trivial FTP (TFTP) is a UDP version of FTP that uses UDP port 69. It is called "trivial" because it is relatively unreliable and inefficient and so is more often used for inter-network communication between routers.
- Telnet (Telecommunications Network) is used to remotely connect to a node. All communications with telnet are in cleartext (even passwords for authentication). Telnet operates on TCP port 23. Except for in lab situations, no longer in use.
- Secure Shell (SSH) is a secure replacement of Telnet. SSH allows terminal emulation in cipher text, which equates to enhanced and increased security. SSH usually operates on TCP port 22.
- Network News Transfer Protocol (NNTP) is a protocol used by client and server software to carry USENET (newsgroup) postings back and forth over a TCP/IP network. NNTP operates on TCP port 119.
- Lightweight Directory Access Protocol (LDAP) is a "Directory Services" protocol allowing a server to act as a central directory for client nodes. LDAP operates on TCP and UDP port 389.
- Network Time Protocol (NTP) allows for synchronizing network time with a server. NTP operates on UDP port 123.
- Post Office Protocol (POP3) is the mailbox protocol allowing users to download mail from a mail server. Once you access it, your client software will download all of your incoming mail and wipe it from the server. POP3 operates on TCP port 110.
- The Internet Message Access Protocol (IMAP) allows for server-based repositories of sent mail and other specialized folders. When using IMAP4 instead of POP3 as your incoming mail protocol, you download very minimal information to your local machine and when you want to access actual incoming mail, you are pulling this directly from the mail server. This allows you to access your mail from virtually anywhere. IMAP4 operates on TCP port 143.
- Simple Mail Transfer Protocol (SMTP) used in conjunction with POP3 or IMAP4 allows for sending/receiving of email. Without it you will only be able to receive mail. SMTP operates on TCP port 25.
- Domain Name System (DNS) resolves easy to read domain names into computer readable IP addresses and operates on UDP port 53.
- Simple Network Management Protocol (SNMP) manages devices on IP networks, such as modems, switches, routers, or printers. Default works on UDP port 161.
Repeaters, bridges, routers
ARP and RARP address translation
Basic addressing
An IP Address is a logical numeric address that is assigned to every single computer, printer, switch, router or any other device that is part of a TCP/IP-based network.
Most of servers and personal computers use Internet Protocol version 4 (IPv4). This uses 32 bits to assign a network address as defined by the four octets of an IP address, up to 255.255.255.255. Each octet is converted to a decimal number (base 10) from 0–255 and separated by a period (a dot). This format is called dotted decimal notation. If not familiar with number conversions, a decent tutorial can be found in http://www.cstutoringcenter.com/tutorials/general/convert.php
For example:
- The IPv4 address 11000000101010000000001100011000 is segmented into 8-bit blocks:
11000000,10101000,00000011and00011000. - Each block is converted to decimal: (128 + 64) = 192, (128 + 32 + 8) = 168, (2 + 1) = 3 and (16 + 8) = 24
- The adjacent octets 192, 168, 3 and 24 are separated by a period: 192.168.3.24
Internet Protocol version 6 (IPv6) was designed to answer the future exhaustion of the IPv4 address pool. IPv4 address space is 32 bits which translates to just above 4 billion addresses. IPv6 address space is 128 bits translating to billions and billions of potential addresses. The protocol has also been upgraded to include new quality of service features and security, but also has its vulnerabilities [2] [3]. IPv6 addresses are represented as eight groups of four hexadecimal digits with the groups being separated by colons, for example 2805:F298:0004:0148:0000:0000:0740:F5E9, but methods to abbreviate this full notation exist http://www.vorteg.info/ipv6-abbreviation-rules/.
IP (network)
TCP (transport)
UDP (transport)
ICMP
Applications
Classful networks and subnetting
Until the introduction of Classless Inter-Domain Routing (CIDR) in 1993 to slow the growth of routing tables on routers across the internet, and to help slow the rapid exhaustion of IPv4 addresses, classful networks were used. You can still find it in tutorials, some networks, and in archeological artifacts such as default subnet mask. In classful adresses, the first one or two bytes (depending on the class of network), generally will indicate the number of the network, the third byte indicates the number of the subnet, and the fourth number indicates the host number.
To subnet a network is to create logical divisions of the network, for example arranged on one floor, building or geographical location. Each device on each subnet is to have an address that logically associates it with the others on the same subnet. This also prevents devices on one subnet from getting confused with hosts on another subnet. Subnetting applies to IP addresses because this is done by borrowing bits from the host portion of the IP address. In a sense, the IP address has three components - the network part, the subnet part and the host part. We can create a subnet by logically grabbing the last bit from the network component of the address and using it to determine the number of subnets required.
To make learning subnetting easier see http://www.subnetting.net/Tutorial.aspx (builds up from no knowledge) and http://www.9tut.com/subnetting-tutorial (starts from knowledge about adressess).
Also, http://www.subnet-calculator.com/ and http://www.subnetmask.info/ and these mental shortcuts:
| Mask | # of subnets | SlashFmt | Class A hosts | Class A mask | Class B hosts | Class B mask | Class C hosts | Class C mask | Class C sub hosts | Class C sub mask |
|---|---|---|---|---|---|---|---|---|---|---|
| 255 | 1 or 256 | /32 | 16,777,214 | 255.0.0.0 | 65,534 | 255.255.0.0 | 254 | 255.255.255.0 | Invalid, 1 address | 255.255.255.255 |
| 254 | 128 | /31 | 33,554,430 | 254.0.0.0 | 131,070 | 255.254.0.0 | 510 | 255.255.254.0 | Invalid, 2 addresses | 255.255.255.254 |
| 252 | 64 | /30 | 67,108,862 | 252.0.0.0 | 262,142 | 255.252.0.0 | 1,022 | 255.255.252.0 | 2 hosts, 4 addresses | 255.255.255.252 |
| 248 | 32 | /29 | 134,217,726 | 248.0.0.0 | 524,286 | 255.248.0.0 | 2,046 | 255.255.248.0 | 6 hosts, 8 addresses | 255.255.255.248 |
| 240 | 16 | /28 | 268,435,454 | 240.0.0.0 | 1,048,574 | 255.240.0.0 | 4,094 | 255.255.240.0 | 14 hosts, 16 addresses | 255.255.255.240 |
| 224 | 8 | /27 | 536,870,910 | 224.0.0.0 | 2,097,150 | 255.224.0.0 | 8,190 | 255.255.224.0 | 30 hosts, 32 addresses | 255.255.255.224 |
| 192 | 4 | /26 | 1,073,741,822 | 192.0.0.0 | 4,194,302 | 255.192.0.0 | 16,382 | 255.255.192.0 | 62 hosts, 64 addresses | 255.255.255.192 |
| 128 | 2 | /25 | 2,147,483,646 | 128.0.0.0 | 8,388,606 | 255.128.0.0 | 32,766 | 255.255.128.0 | 126 hosts, 128 addresses | 255.255.255.128 |
- ↑ IEEE 802 https://en.wikipedia.org/wiki/IEEE_802
- ↑ Routing Loop Attack using IPv6 Automatic Tunnels: Problem Statement and Proposed Mitigations http://tools.ietf.org/html/draft-ietf-v6ops-tunnel-loops-07
- ↑ When moving to IPv6, beware the risks http://gcn.com/articles/2013/03/20/risks-moving-to-ipv6.aspx