Linux security
From Gender and Tech Resources
This page contains some basic security measures specifically for people getting started with linux. Knowing your way around a bit on the kinky linux command-line is required for easily doing these steps. If you run into trouble, find us on IRC.
Contents
Setting up root mail
Installing intrusion detection
You can use a firewall, keep your system softwares up to date, stop all unrequired services, use long and difficult passwords and password managers, and more (see below), there is still a chance that some intruder might get into your system.
When intruders penetrate your system there is a great chance that they will want to make their presence as quiet as possible. To do so, they are most likely to replace some common binaries such as ls, netstat or ps with versions that will not make their presence visible. For example, ls can be replaced with an ls version that won't show the files they created, netstat will not show connections that are used by the intruder, and ps will hide processes the intruder runs. To detect changes like that in your system, you can set up intrusion detection with for example aide or tripwire.
In hostile environments, using aide or tripwire makes sense only if it is installed, fully configured and initialised at the very first boot after an installation from scratch, before ever connecting to the internet or doing anything else. It takes only one attack to install a backdoor. Using tripwire after such an event would guarantee that the back door remains just as open as the day an intruder installed it.
aide
To install aide on a debian based system:
$ sudo apt-get install aide
Open up /etc/default/aide with your favourite editor to change who to send its reports to:
$ sudo geany /etc/default/aide
On occasion after a new install when trying a first run, aide complains the /var/lib/aide/aide.db database is missing. Just do:
$ sudo touch /var/lib/aide/aide.db
tripwire
Turning camera off
Hackers gain access to their victims’ computers with remote-access Trojans (RATs) – malware that gives an intruder administrative control over its targeted computers, including, in this case, the ability to remotely control webcams. It’s an invisibly-installed malware program spread via email attachment or by tricking victims into visiting a booby-trapped site.
Tape the camera. It may even be possible to turn it off in BIOS (depending on your version). Better yet, if you know what driver module is controlling the webcam, you can disable the driver with modprobe -r. Check with:
$ lsmod | grep "uvc"
If stuff like this appears, your webcam device uses an uvc driver http://www.ideasonboard.org/uvc/:
uvcvideo 79005 0 videobuf2_vmalloc 12816 1 uvcvideo videobuf2_core 47787 1 uvcvideo videodev 126451 3 uvcvideo,v4l2_common,videobuf2_core media 18305 2 uvcvideo,videodev usbcore 195340 7 uvcvideo,ums_realtek,usb_storage,ehci_hcd,ehci_pci,usbhid,xhci_hcd
To disable the cam:
$ sudo modprobe -r uvcvideo
To enable the cam:
$ sudo modprobe uvcvideo
If not an uvcvideo driver, try $ sudo lsmod | grep "video" and use the modinfo command to find out more about a particular module:
$ sudo modinfo [modulename]
Then replace the "uvcvideo" in the above modprobe command with the name of your driver module.
To disable the webcam at boot (if file not exists, create it):
$ sudo geany /etc/modprobe.d/blacklist.conf
At bottom of the file add this line: blacklist uvcvideo (or the name of your driver instead of "uvcvideo").
Save the file and reboot. Your webcam is no longer functioning.
Turning microphone off
Open the alsa control panel for muting the microphone:
$ sudo alsamixer
You can also use the same modprobe enabling/disabling method as used above for webcam. This page may be helpful for finding your driver module: http://alsa.opensrc.org/ALSA_modules.
Managing passwords
Using a password manager allows you to load passwords in your clipboard, making it hard to catch it with a keylogger (just in case). And all good password managers allow you to generate passwords, making the passwords independent from your personal preferences and harder to crack. One of the easiest password managers is a GUI tool called keepassx:
$ sudo apt-get install keepassx
It will appear in your menu. A "first steps" tutorial can be found here http://keepass.info/help/base/firststeps.html
Recommendations:
- Keep the database on a removable medium like an encrypted USB stick.
- Use a second encrypted stick to keep a backup of that database on.
- For added security, set up the database to use a password as well as a keyfile.
- Try to always close off the application. It uses a lockfile to prevent access by other processes. Quitting the application removes it. If not, and whenever you get a message that you cannot open your database, check on the USB in the directory where the database resides that there isn't a lockfile blocking access. If there is a lockfile while the database is not open for you, just delete the lockfile.
- On rare occasions a database is truly corrupted. That backup on that other stick, phew. :D
If you want to try your hand at cracking your own (current and new) passwords, try one of these http://sectools.org/tag/pass-audit/
Using a firewall
With a firewall, you can:
- Log hosts scanning services that aren't running
- Limit the services that programs can connect to
- Segregate the local network into trust segments (LAN, DMZ, and Internet)
- Redirect ports to the hosts providing the service (NAT).
If you have a single machine only the first two would be of interest. These are also the two that are most likely to cause issues for a beginning user.
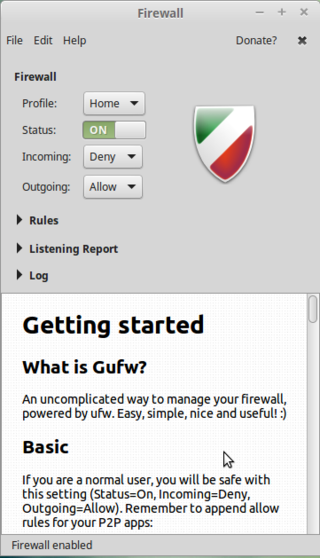
In mint and ubuntu, a firewall is installed, but is disabled by default. Usually it's better to turn it on. Especially on mobile devices like laptops, which sometimes connect to other networks than your own.
The firewall is called Uncomplicated Firewall (ufw), and can be operated from the terminal (Menu > Accessories > Terminal):
$ sudo ufw enable
Type your password when prompted; this will remain entirely invisible, not even asterisks will show, which is normal. Uncomplicated Firewall (ufw) has a sensible set of default settings (profile), which are fine for the vast majority of home users. So unless you have special wishes: you're done!
You can check the status of the firewall with this command:
$ sudo ufw status verbose
If you wish, you can install a GUI frontend to ufw, called gufw:
$ sudo apt-get install gufw
And it'll be in your menu items (the icon is a brick wall).
Safer browsing
...
Encryption
Further hardening of armour
Resources
Related
- Installing linux
- Linux applications
- Kinky linux command-line
- Object encryption on linux
- Anonymising your traffic with linux
- Clean up all the things
- Shell scripting