Difference between revisions of "Detect false mobile antennas"
From Gender and Tech Resources
| Line 134: | Line 134: | ||
== The electromagnetic spectrum == | == The electromagnetic spectrum == | ||
| − | The electromagnetic spectrum or electric radio spectrum is not something material, but the air space | + | The electromagnetic spectrum or electric radio spectrum is not something material, but the air space from the ground to the highest part of the atmosphere. Frequency bands are organized in this space, which airplanes, wi-fi, bluetooth, walkie talkies, radios, and telephones use to communicate, for example 2G, 3G, 4G phone networks all use different bands of the electromagnetic space. |
For more information about the electromagnetic space: | For more information about the electromagnetic space: | ||
| Line 142: | Line 142: | ||
== What is a fake cell tower?== | == What is a fake cell tower?== | ||
Fake cell towers (also known as IMSI catchers) are devices designed to intercept the traffic and possibly track the movements of of a mobile phone by <ref>https://en.wikipedia.org/wiki/IMSI-catcher </ref> pretending to be a "legitimate" cell tower <ref>https://www.eff.org/sls/tech/cell-site-simulators </ref>. | Fake cell towers (also known as IMSI catchers) are devices designed to intercept the traffic and possibly track the movements of of a mobile phone by <ref>https://en.wikipedia.org/wiki/IMSI-catcher </ref> pretending to be a "legitimate" cell tower <ref>https://www.eff.org/sls/tech/cell-site-simulators </ref>. | ||
| − | [[File:Imsi-catcher.png|thumb|none|alt=Esquema torre falsa.| | + | [[File:Imsi-catcher.png|thumb|none|alt=Esquema torre falsa.| Diagram of a fake cell tower (taken from [http://cybernc.com/les-imsi-catchers/ Henri-Olivier]).]] |
| − | IMSI catcher attacks are "man in the middle" attacks <ref>https://en.wikipedia.org/wiki/Man-in-the-middle_attack</ref>. This is defined as an action that gives the attacker the ability to read, insert and modify at will, messages between two parties without either of them knowing that the link between them has been compromised. The attacker | + | IMSI catcher attacks are "man in the middle" attacks <ref>https://en.wikipedia.org/wiki/Man-in-the-middle_attack</ref>. This is defined as an action that gives the attacker the ability to read, insert and modify at will, messages between two parties without either of them knowing that the link between them has been compromised. The attacker is able to observe and intercept messages between the two victims <ref>https://en.wikipedia.org/wiki/IntermediateAccess </ref> |
| − | There is evidence that such devices have been used for surveillance purposes, for example in Ukraine the mobile phones of those attending a large demonstration were tracked and then received a mass text message stating: "Dear subscriber, you have been registered | + | There is evidence that such devices have been used for surveillance purposes, for example in Ukraine the mobile phones of those attending a large demonstration were tracked and then received a mass text message stating: "Dear subscriber, you have been registered as a participant in a mass disturbance "<ref>https://antivigilancia.org/es/2015/06/la-vigilancia-y-la-protesta-social/ </ref>. In Latin America it is known that governments, such as Mexico and Colombia, have bought IMSI Catchers. |
| − | Unfortunately fake cell towers are becoming easier to buy and their price can be as low as 500 USD. Depending on the model there is evidence that IMSI catchers can not only | + | Unfortunately fake cell towers are becoming easier to buy and their price can be as low as 500 USD. Depending on the model there is evidence that IMSI catchers can not only intercept phone traffic, but also can also inject malware. |
| − | + | ==How to detect them? == | |
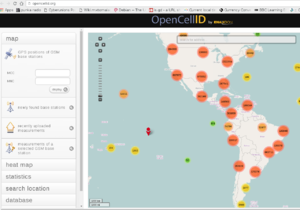
| − | A first step is to have a database of | + | A first step is to have a database of "legitimate" cell towers and the list of legitimate companies that provide these services with the necessary operating permits. In some places these databases exist, such as: http://opencellid.org/ |
| − | [[File:Opencell.png|thumbnail|center| | + | [[File:Opencell.png|thumbnail|center|Towers in Latin America]] |
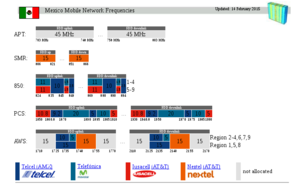
There is also information publicly available about the frequencies on which they should operate: | There is also information publicly available about the frequencies on which they should operate: | ||
| Line 174: | Line 174: | ||
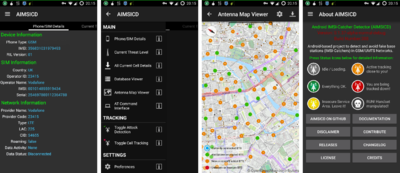
[[File:AIMSICD-Teaser.png|400px|thumbnail|center|AIMSICD]] | [[File:AIMSICD-Teaser.png|400px|thumbnail|center|AIMSICD]] | ||
| − | Android IMSI Catcher Detector attempts to detect IMSI-Catchers through | + | Android IMSI Catcher Detector attempts to detect IMSI-Catchers through methods such as: Check Tower Information Consistency, Check LAC/Cell ID Consistency, check neighbouring cell info, prevent silent app installations, monitor Signal Strength, detect silent SMS and detect FemtoCells |
[https://opensource.srlabs.de/projects/snoopsnitch Snoopsnitch] | [https://opensource.srlabs.de/projects/snoopsnitch Snoopsnitch] | ||
| Line 180: | Line 180: | ||
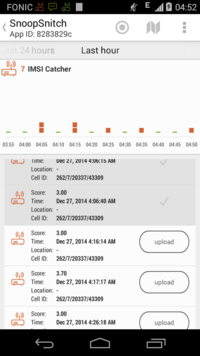
[[File:Sc catcher hour.png|200px|thumbnail|center|Snoopsnitch]] | [[File:Sc catcher hour.png|200px|thumbnail|center|Snoopsnitch]] | ||
| − | SnoopSnitch is an Android app that collects and analyzes mobile radio data | + | SnoopSnitch is an Android app that collects and analyzes mobile radio data and can warn you about threats such as fake base stations (IMSI catchers), user tracking and over-the-air updates. With SnoopSnitch you can use the data collected in the GSM Security Map at gsmmap.org and contribute your own data to GSM Map. This application currently only works on Android phones with a Qualcomm chipset and a stock Android ROM (or a suitable custom ROM with Qualcomm DIAG driver). It also requires root privileges to capture mobile network data. |
== How to protect yourself from fake cell towers?== | == How to protect yourself from fake cell towers?== | ||
| − | Some phones allow you to change their configuration options so that they do not connect to all available cell towers. For example on an Android phone you can go to: Settings > Wireless and networks > More > Mobile networks and there you can change > Preferred network type GSM/UTMS | + | Some phones allow you to change their configuration options so that they do not connect to all available cell towers. For example on an Android phone you can go to: Settings > Wireless and networks > More > Mobile networks and there you can change > Preferred network type GSM/UTMS to using 3G or 4G. Also, if the option is available, choose <Network operators > Select antennas manually. |
You can also isolate your mobile using a Faraday phone pouch, please this tutorial on the topic <ref>https://gendersec.tacticaltech.org/wiki/index.php/Faraday_Phone_Pouch</ref> | You can also isolate your mobile using a Faraday phone pouch, please this tutorial on the topic <ref>https://gendersec.tacticaltech.org/wiki/index.php/Faraday_Phone_Pouch</ref> | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
<gallery> | <gallery> | ||
Revision as of 11:18, 17 March 2017
Contents
- 1 The electromagnetic spectrum
- 2 What is a fake cell tower?
- 3 How to protect yourself from fake cell towers?
- 4 Where can I see more information?
- 5 The electromagnetic spectrum
- 6 What is a fake cell tower?
- 7 How to protect yourself from fake cell towers?
- 8 Where can I see more information?
- 9 The electromagnetic spectrum
- 10 What is a fake cell tower?
- 11 How to detect them?
- 12 How to protect yourself from fake cell towers?
- 13 Where can I see more information?
The electromagnetic spectrum
The electromagnetic spectrum or electric radio spectrum is not something material, but the space that is in the air that goes from the ground to the highest part of the sky. In this space, bands frequencies through which airplanes, wi-fi, bluetooth, walkie talkies, radios, telephones communicate are organized. The fact that our phones can be 2G, 3G, 4G means that they are using different bands of the electromagnetic space, through which the information circulates.
For more information about the electromagnetic space: https://imagine.gsfc.nasa.gov/science/toolbox/emspectrum1.html https://en.wikipedia.org/wiki/Electromagnetic_spectrum
What is a fake cell tower?
Fake cell towers (also known as IMSI catcher) are devices designed to intercept the traffic of a mobile phone and track the movements of the user's phone [1] pretending to be a "legitimate" cell tower [2].
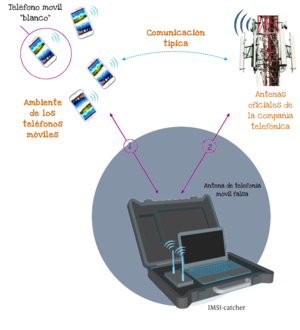
By the way they work IMSI catcher are considered a "man in the middle" attack [3]. This is defined as an attack that acquires the ability to read, insert and modify at will, messages between two parties without any of them knowing that the link between them has been violated. The attacker should be able to observe and intercept messages between the two victims [4]
There is evidence that such devices have been used for surveillance purposes, for example in Ukraine the mobile phones of those attending a large demonstration were tracked and then massively received a text message stating "Dear subscriber, you have been registered As a participant in a mass disturbance "[5]. In Latin America, it is known that governments like Mexico and Colombia have bought such devices.
Unfortunately fake cell towers are becoming easier to get and their price can be as low as $ 500. Depending on the model there is evidence that not only can intercept the traffic of a phone but also can also inject malware.
Bold text==How to detect them? ==
A first step would be to have a database of the "legitimate" cell towers and the list of legitimate companies that provide these services and have the necessary operating permits. There are some databases such as: http://opencellid.org/
There is also information about the frequencies where they should operate: http://www.spectrummonitoring.com/frequencies/frequencies2.html#Mexico
And you can have a look at the development of the GSM network:
http://www.spectrummonitoring.com/frequencies/frequencies2.html#Mexico
There are also some applications that can be downloaded from the following free app repository: F-Droid is a software repository (or "app store") for Android applications, similar to the Google Play store. The main repository, hosted by the project, contains only apps which are free software. Applications can be browsed and installed from the F-Droid website or client app without the need to register for an account. "Anti-features" such as advertising, user tracking, or dependence on non-free software are flagged in app descriptions.[3] The website also offers the source code of applications it hosts as well as the software running the F-Droid server, allowing anyone to set up their own app repository.
In order to detect possible false antennas, you can download from F-Droid the following applications:
Android IMSI Catcher Detector attempts to detect IMSI-Catchers through detection methods such as: Check Tower Information Consistency, Check LAC/Cell ID Consistency, check Neighbouring Cell Info, prevent silent app installations, monitor Signal Strength, detect silent SMS and detect FemtoCells
SnoopSnitch is an Android app that collects and analyzes mobile radio data to make you aware of your mobile network security and to warn you about threats like fake base stations (IMSI catchers), user tracking and over-the-air updates. With SnoopSnitch you can use the data collected in the GSM Security Map at gsmmap.org and contribute your own data to GSM Map. This application currently only works on Android phones with a Qualcomm chipset and a stock Android ROM (or a suitable custom ROM with Qualcomm DIAG driver). It requires root priviliges to capture mobile network data.
How to protect yourself from fake cell towers?
If your phone allows it you can change its configuration options so that it does not connect to all available cell towers. For example on an Android phone you can go to: Configuration > Wireless and networks > More configuration > Mobile networks and there you can change > Network preferences GSM/UTMS for using 3G or 4G if your smart-phone allows it and also choose for > Network operators > Choosing manually the antennas to connect.
You can also isolate your mobile using a Faraday phone pouch, please read this other tutorial on the topic [6]
Where can I see more information?
http://wiki.labomedia.org/index.php/GSM https://quematumovil.pimienta.org/los_imsi-catchers.html
The electromagnetic spectrum
The electromagnetic spectrum or electric radio spectrum is not something material, but the air space that goes from the ground to the highest part of the atmosphere. In this space, frequency bands are organized, through which airplanes, wi-fi, bluetooth, walkie talkies, radios, telephones communicate, for example 2G, 3G, 4G phone networks use different bands of the electromagnetic space, through which data is transmitted.
For more information about the electromagnetic space: https://imagine.gsfc.nasa.gov/science/toolbox/emspectrum1.html https://en.wikipedia.org/wiki/Electromagnetic_spectrum
What is a fake cell tower?
Fake cell towers (also known as IMSI catchers) are devices designed to intercept the traffic of a mobile phone and track the movements of the user's phone [7] pretending to be a "legitimate" cell tower [8].

From the way they work IMSI catchers are considered to execute "man in the middle" attacks [9]. This is defined as an attack that acquires the ability to read, insert and modify at will, messages between two parties without either of them knowing that the link between them has been compromised. The attacker should be able to observe and intercept messages between the two victims [10]
There is evidence that such devices have been used for surveillance purposes, for example in Ukraine the mobile phones of those attending a large demonstration were tracked and then received a mass text message stating: "Dear subscriber, you have been registered As a participant in a mass disturbance "[11]. In Latin America, it is known that governments, such as Mexico and Colombia, have bought such devices.
Unfortunately fake cell towers are becoming easier to get and their price can be as low as 500 USD. Depending on the model there is evidence that IMSI catchers can not only can intercept phone traffic, but also can also inject malware.
Bold text==How to detect them? ==
A first step is to have a database of the "legitimate" cell towers and the list of legitimate companies that provide these services with the necessary operating permits. Some of these databases exist, such as: http://opencellid.org/
There is also information available about the frequencies on which they should operate: http://www.spectrummonitoring.com/frequencies/frequencies2.html#Mexico
And you can have a look at the development of the GSM network:
http://www.spectrummonitoring.com/frequencies/frequencies2.html#Mexico
There are also some applications that can be downloaded from the following free app repository: F-Droid is a software repository (or "app store") for Android applications, similar to the Google Play store. The main repository, hosted by the project, contains only apps which are free software. Applications can be browsed and installed from the F-Droid website or client app without the need to register for an account. "Anti-features" such as advertising, user tracking, or dependence on non-free software are flagged in app descriptions.[3] The website also offers the source code of applications it hosts as well as the software running the F-Droid server, allowing anyone to set up their own app repository.
In order to detect possible false antennas, you can download from F-Droid the following applications:
Android IMSI Catcher Detector attempts to detect IMSI-Catchers through detection methods such as: Check Tower Information Consistency, Check LAC/Cell ID Consistency, check neighbouring cell info, prevent silent app installations, monitor Signal Strength, detect silent SMS and detect FemtoCells
SnoopSnitch is an Android app that collects and analyzes mobile radio data to make you aware of your mobile network security and to warn you about threats such as fake base stations (IMSI catchers), user tracking and over-the-air updates. With SnoopSnitch you can use the data collected in the GSM Security Map at gsmmap.org and contribute your own data to GSM Map. This application currently only works on Android phones with a Qualcomm chipset and a stock Android ROM (or a suitable custom ROM with Qualcomm DIAG driver). It requires root priviliges to capture mobile network data.
How to protect yourself from fake cell towers?
If your phone allows it you can change its configuration options so that it does not connect to all available cell towers. For example on an Android phone you can go to: Configuration > Wireless and networks > More configuration > Mobile networks and there you can change > Network preferences GSM/UTMS for using 3G or 4G if your smart-phone allows it and also choose for > Network operators > Choosing manually the antennas to connect.
You can also isolate your mobile using a Faraday phone pouch, please read this other tutorial on the topic [12]
Where can I see more information?
http://wiki.labomedia.org/index.php/GSM https://quematumovil.pimienta.org/los_imsi-catchers.html
The electromagnetic spectrum
The electromagnetic spectrum or electric radio spectrum is not something material, but the air space from the ground to the highest part of the atmosphere. Frequency bands are organized in this space, which airplanes, wi-fi, bluetooth, walkie talkies, radios, and telephones use to communicate, for example 2G, 3G, 4G phone networks all use different bands of the electromagnetic space.
For more information about the electromagnetic space: https://imagine.gsfc.nasa.gov/science/toolbox/emspectrum1.html https://en.wikipedia.org/wiki/Electromagnetic_spectrum
What is a fake cell tower?
Fake cell towers (also known as IMSI catchers) are devices designed to intercept the traffic and possibly track the movements of of a mobile phone by [13] pretending to be a "legitimate" cell tower [14].

IMSI catcher attacks are "man in the middle" attacks [15]. This is defined as an action that gives the attacker the ability to read, insert and modify at will, messages between two parties without either of them knowing that the link between them has been compromised. The attacker is able to observe and intercept messages between the two victims [16]
There is evidence that such devices have been used for surveillance purposes, for example in Ukraine the mobile phones of those attending a large demonstration were tracked and then received a mass text message stating: "Dear subscriber, you have been registered as a participant in a mass disturbance "[17]. In Latin America it is known that governments, such as Mexico and Colombia, have bought IMSI Catchers.
Unfortunately fake cell towers are becoming easier to buy and their price can be as low as 500 USD. Depending on the model there is evidence that IMSI catchers can not only intercept phone traffic, but also can also inject malware.
How to detect them?
A first step is to have a database of "legitimate" cell towers and the list of legitimate companies that provide these services with the necessary operating permits. In some places these databases exist, such as: http://opencellid.org/
There is also information publicly available about the frequencies on which they should operate: http://www.spectrummonitoring.com/frequencies/frequencies2.html#Mexico
And you can also monitor the development of the GSM network:
http://www.spectrummonitoring.com/frequencies/frequencies2.html#Mexico
There are also some applications that can be downloaded from F-Droid (F-Droid is an alternative to Google Play Centre, where you can download free and open source Android apps independently of Google)
To detect possible false antennas:
Android IMSI Catcher Detector attempts to detect IMSI-Catchers through methods such as: Check Tower Information Consistency, Check LAC/Cell ID Consistency, check neighbouring cell info, prevent silent app installations, monitor Signal Strength, detect silent SMS and detect FemtoCells
SnoopSnitch is an Android app that collects and analyzes mobile radio data and can warn you about threats such as fake base stations (IMSI catchers), user tracking and over-the-air updates. With SnoopSnitch you can use the data collected in the GSM Security Map at gsmmap.org and contribute your own data to GSM Map. This application currently only works on Android phones with a Qualcomm chipset and a stock Android ROM (or a suitable custom ROM with Qualcomm DIAG driver). It also requires root privileges to capture mobile network data.
How to protect yourself from fake cell towers?
Some phones allow you to change their configuration options so that they do not connect to all available cell towers. For example on an Android phone you can go to: Settings > Wireless and networks > More > Mobile networks and there you can change > Preferred network type GSM/UTMS to using 3G or 4G. Also, if the option is available, choose <Network operators > Select antennas manually.
You can also isolate your mobile using a Faraday phone pouch, please this tutorial on the topic [18]
Where can I see more information?
http://wiki.labomedia.org/index.php/GSM
https://quematumovil.pimienta.org/los_imsi-catchers.html- ↑ https://en.wikipedia.org/wiki/IMSI-catcher
- ↑ https://www.eff.org/sls/tech/cell-site-simulators
- ↑ https://en.wikipedia.org/wiki/Man-in-the-middle_attack
- ↑ https://en.wikipedia.org/wiki/IntermediateAccess
- ↑ https://antivigilancia.org/es/2015/06/la-vigilancia-y-la-protesta-social/
- ↑ https://gendersec.tacticaltech.org/wiki/index.php/Faraday_Phone_Pouch
- ↑ https://en.wikipedia.org/wiki/IMSI-catcher
- ↑ https://www.eff.org/sls/tech/cell-site-simulators
- ↑ https://en.wikipedia.org/wiki/Man-in-the-middle_attack
- ↑ https://en.wikipedia.org/wiki/IntermediateAccess
- ↑ https://antivigilancia.org/es/2015/06/la-vigilancia-y-la-protesta-social/
- ↑ https://gendersec.tacticaltech.org/wiki/index.php/Faraday_Phone_Pouch
- ↑ https://en.wikipedia.org/wiki/IMSI-catcher
- ↑ https://www.eff.org/sls/tech/cell-site-simulators
- ↑ https://en.wikipedia.org/wiki/Man-in-the-middle_attack
- ↑ https://en.wikipedia.org/wiki/IntermediateAccess
- ↑ https://antivigilancia.org/es/2015/06/la-vigilancia-y-la-protesta-social/
- ↑ https://gendersec.tacticaltech.org/wiki/index.php/Faraday_Phone_Pouch