Anonymising your traffic with linux
From Gender and Tech Resources
blabla
Contents
Seeing the traffic from and to your machine
Firewall configuration
Kernel modules
Plausible deniability
Plausible deniability in networking is about relaying certain types of broadcasts automatically in such a way that the original transmitter of a file is indistinguishable from those who are merely relaying it allows for the person who first transmitted the file to claim that his computer had merely relayed it from elsewhere, and this claim cannot be disproven without a complete decrypted log of all network connections to and from that person's computer.
And plausible deniability has its limits. Recent cryptographic primitives and protocols offer a wide range of features besides confidentiality and integrity. There are many protocols that have more advanced properties, such as forward secrecy, deniability or anonymity. In a phrack article a deeper look at deniability in communication (e.g. messaging) protocols appeared. One protocol that claims to offer deniability is OTR. The construction in the article can probably be extended in a quite general way. It shows the limits of deniability, especially in protocols that offer message integrity features (as OTR does). A protocol is constructed that enables each partner in a conversation to cooperate with an observing party, such that he can prove the authenticity of any message that was part of the conversation to the observing party [1].
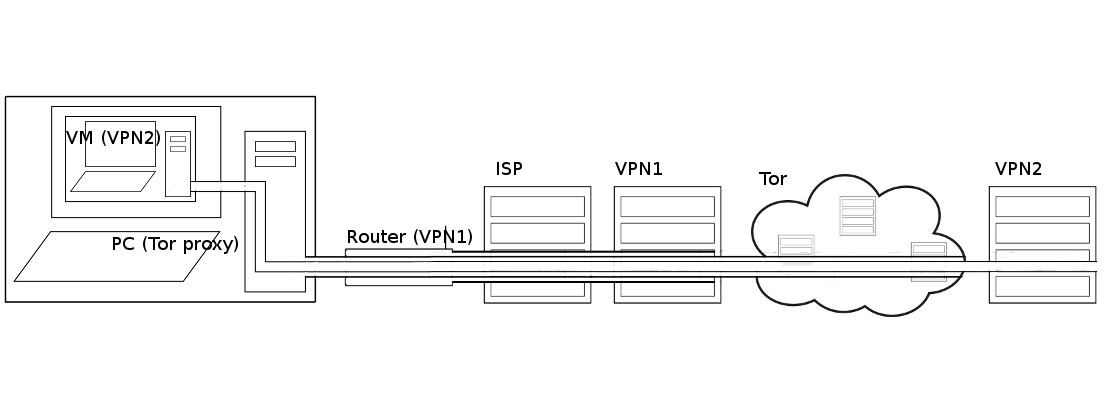
Using virtual private networks
Using SSH tunnels
Using tor
Installing and configuring tor
Liberté linux, tails, whonix, freepto
Which one will work for me?
Liberté linux
See making your own images.
Tails
Whonix
Freepto
Chaining
Going underground with i2p
Related
- ↑ Secure Function Evaluation vs. Deniability in OTR and similar protocols http://phrack.org/issues/68/14.html#article