Difference between revisions of "Anonymising your traffic with linux"
From Gender and Tech Resources
m |
m (→Chaining) |
||
| Line 29: | Line 29: | ||
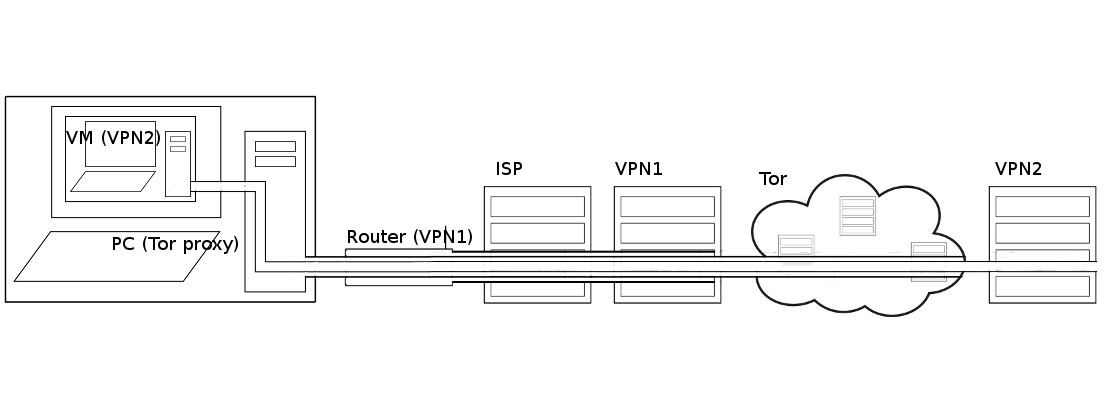
== Chaining == | == Chaining == | ||
| + | |||
| + | [[File:Chaining.jpg|||center]] | ||
== Going underground with i2p == | == Going underground with i2p == | ||
== Related == | == Related == | ||
Revision as of 16:04, 21 June 2015
blabla
Contents
Seeing the traffic from and to your machine
Firewall configuration
Kernel modules
Using virtual private networks
Using SSH tunnels
Using tor
Installing and configuring tor
Liberté linux, tails, whonix, freepto
Which one will work for me?
Liberté linux
See making your own images.