Digital security workshop Les Dégommeuses - Paris
From Gender and Tech Resources
Contents
- 1 Issues about Security, Privacy, Anonymity
- 2 So what ?
- 3 Mapping activities and risks
- 4 Draw your tech day
- 5 Ask yourself good questions
- 6 Secure your devices and data
- 7 What is Internet ?
- 8 How the data are circulating in the network
- 9 Reduce your digital shadow
- 10 Use emails in a safer way
- 11 Preserve your anonymity, circumvent censorship
- 12 Social network
- 13 Mobile / Smart Phone
- 14 Specific questions
- 15 Good practices, a synthesis
- 16 Identifying good resources
Issues about Security, Privacy, Anonymity
- Data and states
- Data and companies
- Data and citizens
- Data and art
So what ?
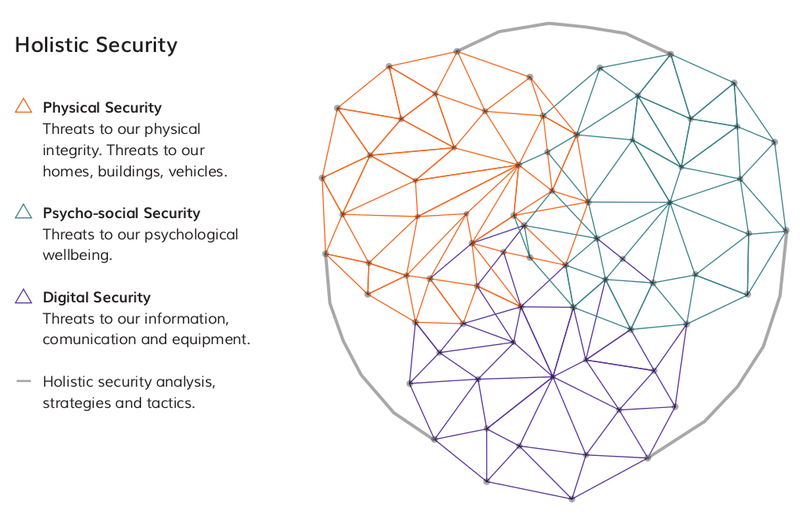
- Holistic security : Physical security + Psycho-social security + digital security http://holistic-security.org/
- A global recipe : Autonomous infrastructures - Free Libre Open Source Softwares - end to end encryption
- Make some noise ! encrypt to increase the cost of surveillance
Mapping activities and risks
Cloud of ideas and words related to security > questions to establish a baseline of privacy and security knowledge
Draw your tech day
Draw your interactions with your digital devices, from the morning to the moment you go to bed, including what kind of data you receive, you produce, you transfert and exchange with other people
Ask yourself good questions
- Read up and educate yourself about your country's internet laws and policies. Some security technologies such as encryption are illegal in some countries, for example.
- Inform yourself about your country's laws and policies in relation to freedom of expression, right to privacy and against online and offline harassment. Those laws do not exist in all countries, and when they exist they are not framed and applied in the same way.
- Keep your computer and devices clean and healthy: Updating your software, running a firewall, and protecting yourself from virus infection are fundamental to the security of your data
- Map your data: What kind of data do you produce and/or manage? With whom? Where is this data stored? Which devices or online platforms hold your data? Most importantly, how sensitive is your data and what would happen if this particular data suddenly disappeared or was seen and copied by a third party?
- Secure your data: Especially where our data is stored online, it is crucial to choose strong passwords, or better passphrases, and to use a different one for each of our accounts.
- Connect safely to the internet: When going online, especially if you are transmitting personal data and passwords, it is crucial to always use an encrypted connection which ensures that your data cannot be seen by anyone as it travels from your computer to the website you are visiting or to the service you are using.
- Anonymise your connections: There are sometimes good reasons to hide your physical location and your internet activities. Tor browser anonymises your connections when you're browsing the internet, by hiding the sites you are visiting from your internet service provider, and hiding your location from the sites you visit.
- Secure your communications: you might want to consider tools you can use and ways you can change your behavior to increase your security when using mobile phones as well as options for email and instant messaging
- Practice self-care: Nothing is secure if we only think about technology and we neglect our wellbeing. If you are exhausted, stressed or burnt out, you might make mistakes that impair your security.
You should repeat periodically this exercise of permanent risk analysis so as to update the threat model and the answers you could put into practice
Secure your devices and data
Computer
- Switch your computer to linux ;)
- Protect your computer against malware and virus https://securityinabox.org/en/guide/malware
- Protect your information from physical threats https://securityinabox.org/en/guide/physical
- Create and maintain secure passwords https://securityinabox.org/en/guide/passwords
- Destroy sensitive information https://securityinabox.org/en/guide/destroy-sensitive-information
Mobile phone / tablet
- Use mobile phones as securely as possible https://securityinabox.org/en/guide/mobile-phones
- Use smartphones as securely as possible https://securityinabox.org/en/guide/smartphones
- Encrypt your mobile phone, basic Android security setup guide https://securityinabox.org/en/guide/basic-setup/android
What is Internet ?
A network of networks of computers : Your computer > Internet Service Provider > router > gateway > backbone > sever serveur / routeur
- http://maps.level3.com/default/ ou http://www.submarinecablemap.com/#/landing-point/marseille-france
- http://www.teliasoneraicmap.com/
- http://www.vox.com/a/internet-maps 40 maps that explain the internet
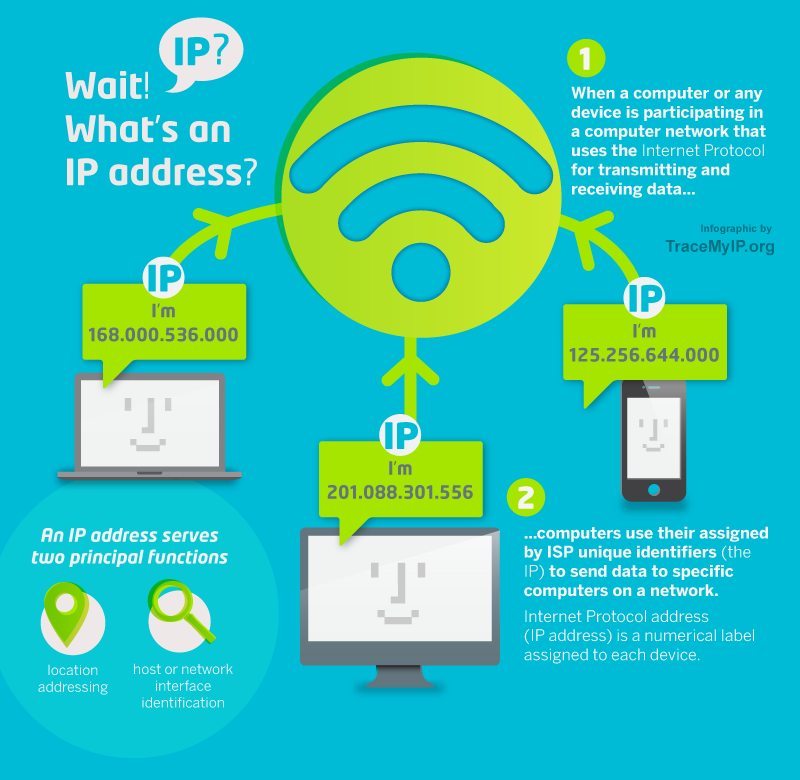
What is an IP address ?
An IP address identify your computer inside a local network (it is a private IP, for example 192.168.1.101), then your internet box provide you a public IP address connected to Internet (for example 82.239.0.211). Each network devices is identfied by a unique physical address called the MAC address (for example f4:6d:04:3a:ef:55)
- visualize your ip address and the geolocalization of your computer http://whatismyipaddress.com/
- demo traceroute : visualize where your traffic is going http://www.yougetsignal.com/tools/visual-tracert/
How the data are circulating in the network
If you tried the previous link, you can see that your request reach a server that can be on the other side if the world. But there are third parties that collect informations and datas on your navigation, most of the time to gather informations about you and to sell it for commercial purposes (we call them data brokers), so in function of the website, one single request can be tracked by up to more than twenty other companies ...
- https://trackography.org/ > Choose a country and a newspaper and see who is collecting data when you go to this website
Internet role play
Each person become an element of the network :
- Computer A
- ISP box at home
- Gateway to Internet
- Backbone
- Trans-oceanic cable
- Gmail server
- Autonomous Tchat server
- Public wifi access point
- Computer B
Now, let's send a "normal" e-mail from computer A to computer B and let's see who can read what between metadatas and the content of the mail. Repeat the exercise with an encrypted e-mail, with a normal tchat and an encrypted tchat
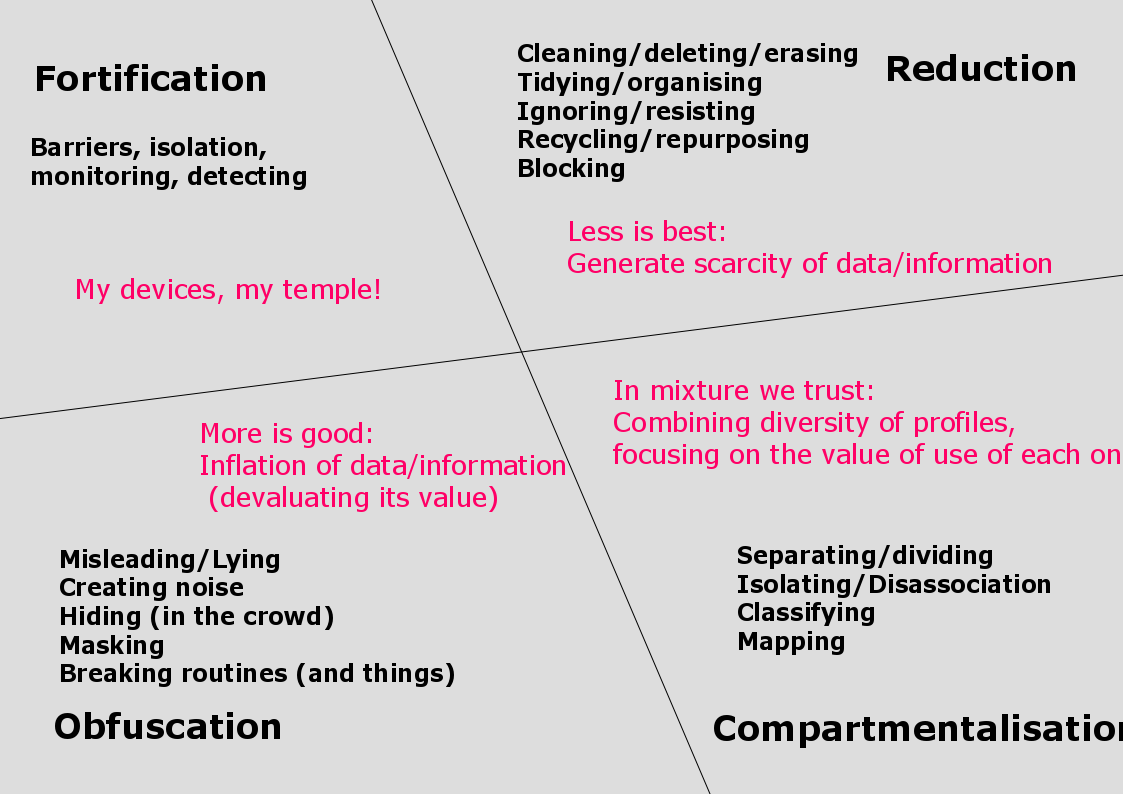
Reduce your digital shadow
The web - Browser and plug-ins
- To remove adds : ublock origin https://addons.mozilla.org/en-US/firefox/addon/ublock-origin/
- To prevent tracking : betterprivacy https://addons.mozilla.org/en-US/firefox/addon/betterprivacy/
- To reduce our digital shadow : Privacy Badger https://www.eff.org/privacybadger
- To use as much as possible encrypted communication between our computer and the server : HTTPS everywhere https://www.eff.org/https-everywhere
- To avoid viruses from web pages and javascript https://noscript.net/
- To avoid viruses from Flash content : flashblock https://addons.mozilla.org/en-US/firefox/addon/flashblock/
Alternative search engines
To add a new search engine to Firefox, see https://support.mozilla.org/en-US/kb/add-or-remove-search-engine-firefox
- https://duckduckgo.com/ see also the bangs https://duckduckgo.com/bang : if you add "!w" to your request, it will search directly on wikipedia
- https://www.qwant.com/
- https://startpage.com/
- https://searx.laquadrature.net/ meta hackable search engine
Evaluate the traceability of your system and browser
The "fingerprinting" allow one to identify us in function of our configuration : operating system, browser configuration, plug-ins, size of our screen, ...
- to make a test : Panopticlick http://panopticlick.eff.org/
Remove metadata from files
Metadata are included in pictures, text documents, videos, and can include geolocalization, the name of the autor and many more informations
- see the tool Exiftool : to remove metadata :
exiftool "-all:all=petit chaton" -overwrite_original *.ogg
Use emails in a safer way
Alternative email providers
- https://help.riseup.net/
- http://no-log.org/
- http://autistici.org
- https://www.openmailbox.org/
- https://mailinabox.email/
Disposable emails
- https://www.guerrillamail.com/
- https://www.sharklasers.com/
- http://maildrop.cc/
- http://throwawaymail.com/
- http://yopmail.com/
- http://clipmail.eu
- https://addons.mozilla.org/fr/firefox/addon/bloody-vikings/
Encrypt mails with PGP
With a combination of thunderbird and enigmail plug-in :
- PGP avec enigmail et thunderbird https://securityinabox.org/en/guide/thunderbird/windows
- Tutorial from FSF https://emailselfdefense.fsf.org/en/
- 15 reasons not to start using PGP http://secushare.org/PGP
Communication and exchange services
Let's use alternative services without any commercial purposes FLOSS (Free/Libre Open Source), to replace skype, dropbox, doodle, google doc, ... :
- Dégoogleise Internet https://degooglisons-internet.org/
Tchat
- pidgin with à OTR https://otr.cypherpunks.ca/
- https://crypto.cat/
- https://pond.imperialviolet.org/
- https://ricochet.im/
- https://blog.torproject.org/blog/tor-messenger-beta-chat-over-tor-easily
Visioconference
- chat with visioconference with jit.s https://jitsi.org/Main/Download / installation : https://jitsi.org/Documentation/SetUpJitsiAccount / open an account https://jit.si/
- directly in the browser : https://meet.jit.si/ or https://www.mozilla.org/fr/firefox/hello/
- Tox to replace skype https://tox.im/
Preserve your anonymity, circumvent censorship
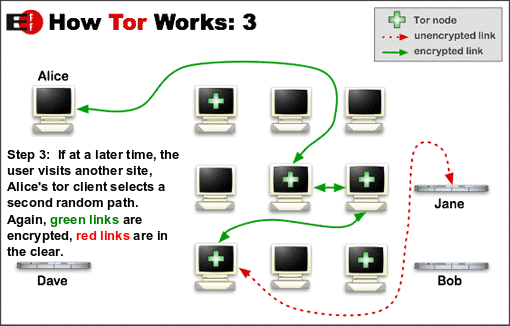
Use Tor (The Onion Router), Tails (Live Linux amnesic operating system), a VPN (create a tunnel between you and your vpn provider)
- TOR : https://www.torproject.org/projects/torbrowser.html.en
- TAILS : https://tails.boum.org/install/
- VPN : https://help.riseup.net/fr/vpn
Understand the difference between encryption and anonymity
- video gpg tactical tech https://tacticaltech.org/projects/decrypting-encryption https://vimeo.com/132517596
- tor browser : https://www.youtube.com/user/TheTorProject
Social network
Let's ask some good questions
How is the web service on which I'm willing to sign in is earning money ? What is its economical model ?
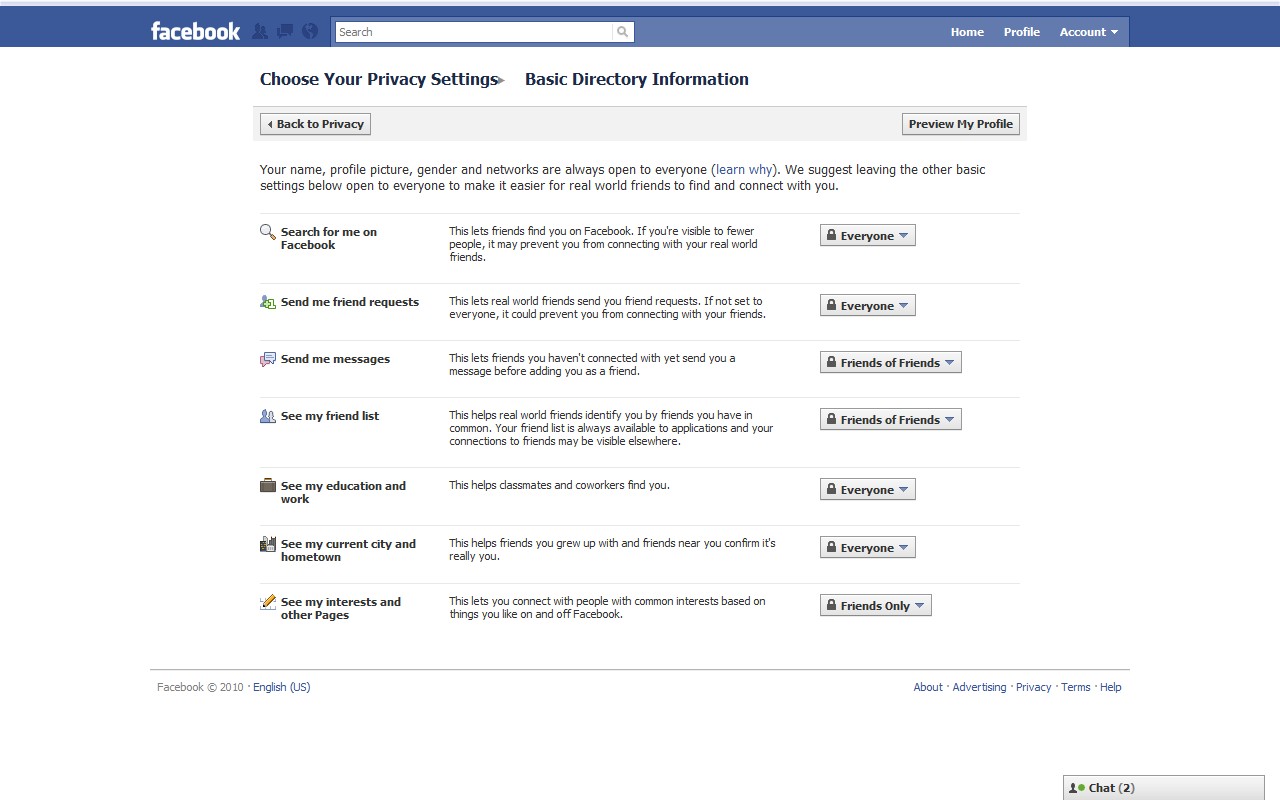
Set up the privacy settings of your account, strong passwords, use d'https
Define which kind of information you are publishing, did everybody agreed ? :
- who can see the informations I published
- Who is the owner of the information I published
- What kind of personal informations can I transfer to other people
- Are my contacts ok with the fact that I share informations about them with others ?
- Do I trust all the persons with which I'm in contact ?
Consider that event if you are not inscribed on Facebook, Facebook will build a shadow profile about you (Friends inviting me on facebook ...), be careful when using your Facebook or google account to sign in another web service
Choose between 4 strategies concerning your on-line identity
- Real name
- Risk: Using your "real world" identity online means you are easily identifiable by family members, colleagues, and others, and your activities can be linked back to your identity.
- Reputation: Others can easily identify you, thus gaining reputation and trust is easier.
- Effort: It requires little effort.
- Total anonymity
- Risk: It can be beneficial at times, but also be very difficult to maintain. Choose this option carefully.
- Reputation: There are few opportunities to network with others thus to gain trust and reputation.
- Effort: Intensive as it requires considerable caution and knowledge. It will probably require the use of anonymisation tools (for example Tor or TAILS)
- Persistent pseudonymity
- *Risk: Pseudonyms could be linked to your real world identity.
- Reputation: A persistent pseudonym that others can use to identify you across platforms is a good way to gain reputation and trust.
- Effort: Maintenance requires some effort, particularly if you are also using your real name elsewhere.
- Collective Identity
- Risk: Possible exposure of your real world identity by other people's actions in the group.
- Reputation: While not a way to gain individual reputation, you can still benefit from the reputation of the collective.
- Effort: Although secure communications are still important, it requires less effort than total anonymity.
More about this question : https://gendersec.tacticaltech.org/wiki/index.php/Complete_manual#Creating_and_managing_identities_online
4 strategies to alter our digital shadow
Mobile / Smart Phone
How a mobile phone is working, triangulation, autorisations asked by applications, metadata, alternative operating system, signed applciations, rooting and jailbreaking
Encrypt your phone, pass phrase, use FLOSS applications
Recommended softwares to communicate and exchange :
- See the market dedicated to Free Libre Open Source applications http://f-droid.org/
- And the applications developed by par https://guardianproject.info/ (available in f-droid)
Mobile applications renowned as safe in june 2016
Always check on https://securityinabox.org/en/mobile-tools to see if an application is still safe
- SMSSecure
- Signal
- Telegraph et Snapchat (not FLOSS but end to end encryption)
- Orbot + Orweb (web browsing threw Tor network)
- keepassDroid
- Android Privacy Guard (emails + GPG)
- Obscuracam to hide people's face
Free your phone
- Free your Android : http://fsfe.org/campaigns/android/liberate.fr.html + http://www.gnu.org/philosophy/android-and-users-freedom.html
Specific questions
How can I ask Google to forget about me
- At least in Europe https://support.google.com/legal/contact/lr_eudpa?product=websearch
How can I create a mobile application from a responsive design web site
At the end, no straight easy answer (yet), some resources :
- With Cordova https://github.com/MobileChromeApps/mobile-chrome-apps and http://taco.visualstudio.com/en-us/docs/create-a-hosted-app/
Good practices, a synthesis
Backup, strong pass phrase, FLOSS Opératiing system and softwares, Autonomous infrastructure (Yunohost, non commercial), holistic security, update of the threat model network of trust, Safe spaces
After the workshop, what would you
- Start
- Stop
- Keep
doing ...
Identifying good resources
- Security in a box https://securityinabox.org/ tools revised by a pool of digital security trainers, download the software from there
- Me and my shadow https://myshadow.org/ tips for mobile phone and browser
- Zen manual https://gendersec.tacticaltech.org/wiki/index.php/Complete_manual focused on the gender and tech question : on-line identities, safe spaces, ...
- Holistic security : Physical security, Psycho-social security, digital security https://holistic-security.tacticaltech.org/
- About Dating apps : https://www.eff.org/deeplinks/2012/02/comparing-privacy-and-security-online-dating-sites http://www.forbrukerradet.no/appfail-en/ https://grindrmap.neocities.org/overview.html
- A webserie about privacy, big data, surveillance ... "Do not track me" https://donottrack-doc.com/en/episodes/